If something doesn't exist, it can't be detected
Tuesday, July 26, 2016
2 – 2 = 0
3 – 3 = 0
2 – 2 = 3 – 3
2 = 3
Mathematical fallacy
Sophism is a complex argument designed to confuse or mislead an opponent.
What is a virus? In a nutshell, it's a file that does something a criminal needs it to do.
A file monitor (in Dr.Web's case, this is SpIDer Guard) detects malicious files.
The Dr.Web SpIDer Guard component is incorporated into the Dr.Web Anti-virus.
Therefore, the product provides sufficient protection from malware.
An anti-virus fallacy
The logic appears flawless, and yet it is flawed. Indeed, most malware species exist as files. However, some of them don’t.
For starters, there are worms—they existed at the very dawn of virus making. And what about rootkits? And malware for BIOS. Attackers never stop trying to escape the attention of this component, which is present in all anti-viruses.
There exists a special category of modern Trojans that security experts refer to as bodiless or file-less malware. They do not exist on an infected computer as separate files and reside only in the memory. To store themselves, they use various storage containers such as the Windows registry.
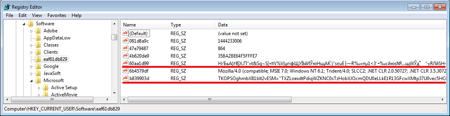
For example, the polymorphic malicious program Trojan.Kovter.297 creates several registry entries: one of them contains its encrypted body, while the other is a script that decrypts it and loads into the memory. The names of these entries contain special characters that prevent the registry editor from displaying them.
Actually Trojan.Kovter operates in the RAM of an infected system and doesn't copy itself to a disk as a separate file which, to a certain extent, complicates its detection and neutralisation.
It should be noted that although malware stores itself in multiple parts in the registry, and this makes it more complicated for a signature-based file monitor to detect it, the technologies incorporated into Dr.Web enable it to accomplish this task.
There are also other options. As you know, many modern solutions (Adobe, browsers, Microsoft Office) support macros, scripts, etc. — small programs. JavaScript is used on many sites to facilitate better interaction with users. The scripts are run by browsers and text processors and don't need to be saved on a hard drive.
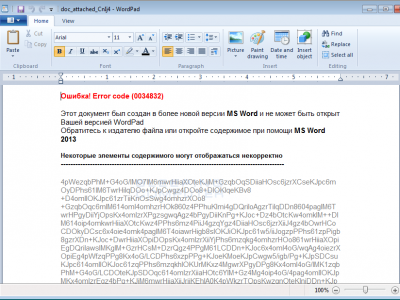
The encryption ransomware Trojan.Encoder.4860 is written entirely in JavaScript and is spread as a JS file. To complicate its analysis, the code is obfuscated—its pieces are placed in a haphazard order to make it harder for signature-based analysis to detect it. As a distraction, the Trojan creates a Word document containing pieces of text from other files and opens it to convince the user that the document has been damaged. The library CryptoJS is used to encrypt files.
For now, Trojan.Encoder.4860 encrypts 16 types of files (.doc, .xls, .rtf, .pdf, .dbf, .jpg, .dwg, .cdr, .psd, .cd, .mdb, .png, .lcd, .zip, .rar и .csv) and changes the extensions to .locked. Criminals demand a ransom of 0.39 bitcoins (about $250 at the current exchange rate) from victims.
Attackers spread Trojan.Encoder.4860 with spam messages containing a .js file disguised as an Office document that the user is meant to open. In most systems, the script is run by means of Windows Script Host which provides it with access to all system utilities.
The Anti-virus Times recommends
Use the traffic scanning components Dr.Web SpIDer Gate and Dr.Web SpIDer Mail, which can be found in Dr.Web Security Space, to check mail and web traffic before they are received by the respective applications.
To access SpIDer Gate settings, click the icon
 in the system tray. In the pop-up menu, click on the padlock icon
in the system tray. In the pop-up menu, click on the padlock icon  ( Administrator mode), and click on the gears icon
( Administrator mode), and click on the gears icon  ( Settings). In the Settings window, select Protection components→SpIDer Gаte.
( Settings). In the Settings window, select Protection components→SpIDer Gаte.Important! The anti-virus settings may be password-protected.
Dr.Web anti-viruses also use Dr.Web ScriptHeuristic technologies that enable them to detect obfuscated exploits in HTML and PDF files containing JavaScript code. ScriptHeuristic prevents any malicious browser scripts and PDF documents from being executed, without disabling the functionality of legitimate scripts. It protects against infection by unknown viruses that try to access systems via web browsers. It works independently of the Dr.Web virus databases, in any web browser.
- Disable the option that enables the mail client to send and receive executable files. By default, Microsoft Outlook blocks certain types of files (e.g., EXE-files) attached to messages because they may contain malware that poses a threat to the system. По умолчанию программа Outlook блокирует такие файлы. A complete list of blocked file types can be found here.
- If you need to run scripts and macros for your work, you can disable the option in office suites and PDF viewers. You can learn how to do this in MS Office here.



![Shared 16 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
vasvet
12:47:41 2018-07-15