The autopsy will reveal all
Monday, March 27, 2017
When people say "anti-virus", they often talk about “signatures”. However, exposing a culprit is only part of the job. The investigation must also determine accomplices and victims. In other words, detecting a malicious file is not enough. An anti-virus should also be able to find the resources being used by the malware. This can be particularly important for heuristic analysis—knowing how typical malware behaves can prevent the newest modifications of that malware from causing a repeat infection and help configure the anti-spam, the Parental Control's black lists, and firewall rules.
And, if in most cases signatures can be obtained relatively quickly (if, of course, a malicious program has one), behaviour analysis is a lengthy process, and when you read a news post about the latest malware, understand that its short description required weeks of work by analysts.
To examine malicious files, analysts use special software that includes solutions available to everyone as well as tools that have been specifically designed in an anti-virus laboratory for this purpose. There are quite a few programs of this kind. Let's talk about some of the categories they fall into.
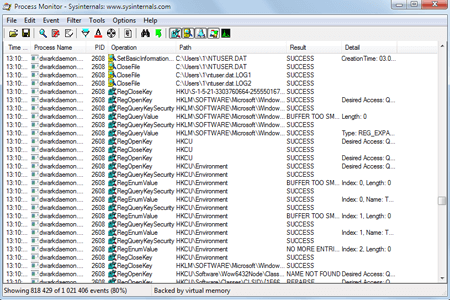
Everyone can perform an initial program analysis (although we don't recommend it). For example, the free utility Procmon (Process Monitor) can show in real time what resources are being used by a specific application.
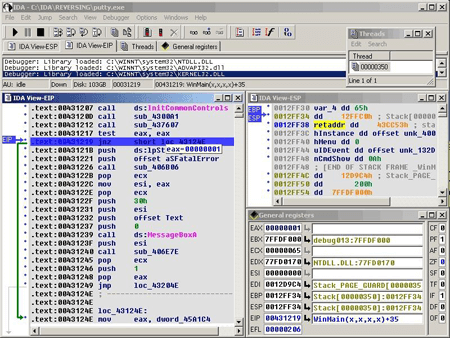
Disassemblers are also used for analysis. Virtually any analysed file (except scripts) is a set of CPU instructions.
A disassembler works with executable files or code stored in some buffer. Finding an ingress point is an important stage in disassembly. From this point file analysis begins. For example, it can be the starting point of the malicious code that was deployed by malware into a healthy file.
The disassembler commences analysis from the ingress point, determines what kind of instruction it is and its length in bytes, and checks whether it is a jump instruction and which memory segment it addresses, etc. Having analysed one instruction, the disassembler switches to the next one or, if the analysed code was a jump instruction, it moves to the specified address. If the instruction is a conditional jump, the disassembler will designate two addresses—the address of the subsequent instruction as well as the address to which execution is supposed to move. If the disassembler fails to interpret a byte sequence, it stops analysing the branch.
ДThe disassembler turns byte sequences into a human-readable format. The resulting output contains information about the actions to be performed and the data being used as well as addresses from which this instruction is called.
https://ru-sf.ru/threads/delaem-svoj-virlab-vvedenie.3162
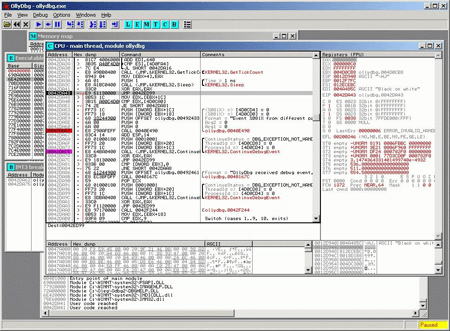
The problem is that the code it needs to analyse may be inaccessible until it starts being executed. In situations of this kind, a debugger may come to the rescue.
A debugger controls the operation of a running program, and whenever it performs an action, the debugger will stop its execution. A debugger can operate in two modes: in the first one it will await for a specific moment from which the analysis will start, while the second one involves a step-by-step examination that is somewhat similar to disassembling. However, a disassembler analyses the code of a program that isn't currently running, i.e., it works with the application's file, but a debugger examines a running process (although it will make use of additional information that may help it understand the analysed program's structure). So if a disassembler will only indicate that a conditional branch exists and leave it to the analyst to decide which way the execution will proceed, a debugger will automatically move to the designated instruction sequence, and the analyst will be able to understand why the execution moved to a different piece of code.
https://ru-sf.ru/threads/delaem-svoj-virlab-vvedenie.3162 #anti-virus #Dr.Web_technologies
The Anti-virus Times recommends
A modern anti-virus is a very complex solution that has been battle-hardened by fights with generations of malicious programs. Today there are few companies that can actually design an anti-virus.


![Shared 16 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
vasvet
18:15:50 2018-07-24
Неуёмный Обыватель
04:06:40 2017-03-27