Dirty remote tricks
Friday, January 20, 2017
Enabling remote access to a machine is risky especially if the machine stores important corporate data. If the machine is used by a senior financial officer, any infiltration of the system by criminals will have dire consequences. But should ordinary users fear remote attackers?
We have an online store, some bank cards, and the desire to make money.
Safety first.
We need a (dedicated servise).
We need it:
- for security reasons
- to bypass protection (if it is being used).
Simply put: you can try to register as Michael Jackson from NEW YORK, but your IP indicates that you are somewhere in Romania. The online store realises that something is wrong, and your order will never be processed. So you need your IP to match the information you provide. With a dedicated service, you will achieve just that. You can also use Socks 4-5.
If you choose to use a dedicated service, you will be provided with the following information: 93.161.124.158 login/password
In Windows, use: Remote Desktop Connection. Enter the IP address, login, and password, and you’re there.
You can choose a dedicated service host that resides in a specific country, state, or city. Essentially, you are renting a computer in any part of the world for your personal gain.
Here we've just quoted a post on a hacker site. We can't provide the URL because while we were preparing the issue, the site kicked the bucket—sites of this kind never last too long.
And here’s why. Stealing money is only part of the job. After that you need to launder it. Buying something and reselling it is one way to do that. However, specifying one's own name in a purchase order can be risky. But with remote access, criminals can purchase goods on your behalf from your computer. They can also use it to mount attacks on other machines.
Do you want it to look like Russia/USA/any other country was responsible for the attack? Carry out the attack from the computers of its citizens and everyone will believe just that. After the attack, smart hackers will remove all traces of their presence, and it will be up to you to prove that it wasn't you who had some fun with friends and tried to hack the website of the President/CIA/MO/NASA just to show you could.
By the way, the very presence of cracked programs and hacking software on your computer can be used in court as evidence to prove that you had the capability to conduct unlawful actions.
Once they have remote access, criminals can purchase goods and services on your behalf using logins and passwords you saved with a browser password manager or some other program that performs similar tasks.
Criminals will be able to see everything you type.
A five-year-old managed to memorize all the credit card information his careless Dad entered in a web form. Soon the child started using the information to buy things.
The Anti-virus Times recommends
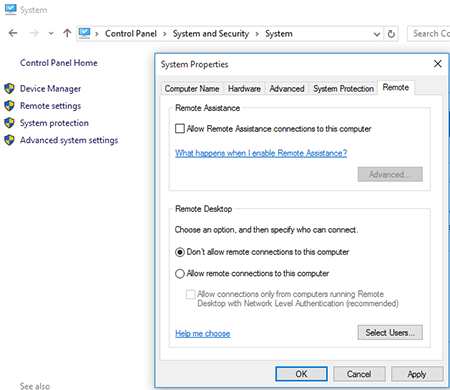
If you don't use remote access services, disable them.
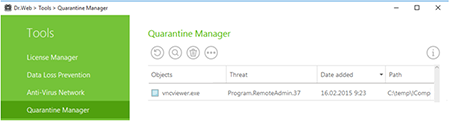
Because remote access can be facilitated with special software, perform a full anti-virus scan of your system. The anti-virus will pick out software used to access computers remotely and prompt you to delete it.
- If you use services of this kind (e.g., you access your home network from your office), restrict the list of machines to which access is granted. Use a strong password and change it regularly.


![Shared 15 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
Неуёмный Обыватель
05:14:34 2018-08-24
vasvet
12:29:40 2018-07-15