A suspect isn't necessarily guilty!
Wednesday, October 19, 2016
An anti-virus consists of multiple components. The anti-virus engine (which receives requests from other components), the behavioural analyser, and cloud technologies (which use statistics showing how programs are operating on multiple hosts) can perform a direct analysis of malware programs.
Suppose a certain program starts requesting access to user data or starts processing a large number of files. What’s at work here? Is it spyware or a program that secures confidential information? Encryption ransomware or a legitimate encryption application?
How can an anti-virus tell malware from legitimate programs?
Anti-virus analysts and programmers have a great responsibility. If an anti-virus mistakes a rarely used file for malware, it’s somewhat unpleasant, but doesn’t do much harm. A user can add the program onto an exception list, restore the file from the quarantine, or choose the correct action to be taken when prompted by the anti-virus.
If the anti-virus wrongly recognises a system component or a component of its own (incidents of this kind occurred many times) as malware, the adverse impact will be far greater. The system can be rendered non-operational. Imagine if this happens, say, to half of all the computers in China!
Why do anti-virus false positives occur?
There exist many reasons.
- The growing number of malicious files means that virus analysts may not have enough time to examine them (including their design and behaviour). Heuristic technologies, which enable anti-viruses to use information about various types of malware in order to assess how dangerous a file may be, are one way around this. Heuristic technologies can use a single entry to detect thousands of malicious programs. However, when designing heuristic analysis routines, developers must avoid a number of pitfalls:
- A heuristic analyser that is too suspicious can cause false positives—if the program being analysed contains pieces of code that are typical of malware.
- A cautious heuristic analyser can easily be circumvented. As a rule, malware makers test their programs against the most popular anti-virus solutions before releasing them into the wild. They alter program code to make sure that it stays invisible to anti-viruses.
- The need to release updates as soon as possible (users are waiting!) also limits the amount of time spent developing and testing cures. Naturally, tests are automated, and the number of test system configurations is growing constantly, but there’s no way to check them all.
- Legitimate software updates. Alas, users don’t always update their software in a timely manner, and meanwhile, the latest updates are always installed on machines involved in anti-virus testing.
Users make mistakes too. Sometimes an anti-virus lets them choose what action to take with a certain file, and they make the wrong choice. Unfortunately, programmers who’ve written a suspicious program could have equipped it with malicious features as well as with useful ones. Many times software updates have resulted in data getting corrupted. Of course, this didn't happen because of ill intent, but sometimes malware makers can distribute malware in the guise of legitimate applications.
The Anti-virus Times recommends
- If you suspect a false positive, notify the anti-virus laboratory. If you use Dr.Web, you can do this at https://vms.drweb.com/sendvirus/?lng=en. Provide as much information about the suspicious program as possible. If you downloaded and installed the program on your own, please specify the download source on the Internet. If an error occurs while certain actions are being performed, describe them. This will make it quicker to solve the problem.
- If your anti-virus notifies you about a probable threat, do the following:
- Update the anti-virus and run a full system scan.
- Limit your interaction with your friends and business partners until the situation is clarified. They won't be happy if, along with receiving news of your problems, they get a Trojan to boot.
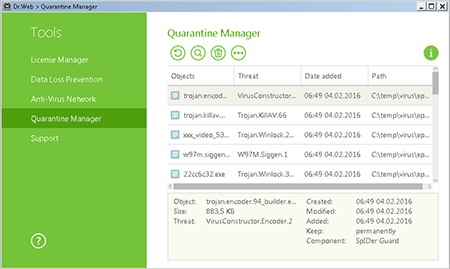
As a rule, suspicious programs are moved to the quarantine (not deleted), although you can set up your anti-virus to perform a different action. To restore a file from the quarantine, in the Dr.Web agent menu, select Tools → Quarantine Manager. A table containing information about the current status of the quarantine will be displayed.
Only users who have permission to access the files can see the corresponding objects in the quarantine. Administrative privileges are required to view hidden objects.
Check the boxes next to the names of the objects you need to restore, and then in the context menu, select Restore (move the file with the specified name into the appropriate folder);
Important! Restore files only if you are absolutely sure that they are harmless!
Important! If the quarantine runs out of space, the files located within it can be deleted. Make sure that free disk space is available in your system.
No anti-virus developer can boast that their product has never detected any false positivesâwe donât claim that our products are error free. We merely do our best to make sure that our technologies make as few mistakes as possible!


![Shared 17 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
Неуёмный Обыватель
04:16:44 2018-08-22
vasvet
06:19:22 2018-07-25