From Melissa Kournikova, with love
Friday, September 16, 2016
Can a problem exist if the media isn’t covering it? For example, every day one comes across news about encryption ransomware; you’d have to be living off the grid to not have heard about it. And many people today are even aware that they need to back up their important information if they want to keep encryption ransomware at bay (of course, knowing and actually doing are two different things☺)! Meanwhile…
ILOVEYOU, a.k.a. LoveLetter, was sent via email from the Philippines on May 5, 2000. If someone opened the attachment, the malware would forward itself to all the addresses found in that person’s Microsoft Outlook address book. Overall, three million computers worldwide were affected by the virus. The damage inflicted on the world’s economy by the malware was estimated to be around $10 billion to $15 billion. ILOVEYOU entered the Book of Guinness World Records as the most destructive computer virus in the world.
Worms of the past: Melissa, Kournikova, ILOVEYOU. Yes, there were worms in our day, but they were nothing like the ones today—these are on steroids! Major news stories about similar types of mailings haven’t been in the news for a long time. Does that mean there aren't any?
Win32.HLLM.MyDoom landed in the Dr.Web virus database in 2006. Its modifications, such as 33808 и 54464, are still found in the wild!
Win32.HLLM.Yaha was originally discovered in 2003. Yet its various modifications persisted for over a decade (e.g., Win32.HLLM.Yaha.42496 was added into the virus database on 10.04.2014)!
How does a system get infected via email? A user either opens an attachment or clicks on a link in a message. Or a mail client performs the action automatically. Of course, the program will only do so if instructed by malware that managed to get into the mail. The message must also be in HTML format and contain JavaScript or ActiveX code. And it also has to bypass an anti-virus check and get into a mailbox.
If vulnerabilities exist in a program, the malicious code in a message can be executed even if the user has not opened it—just receiving the message is enough!
Hackers of the past usually exploited MS Outlook vulnerabilities. Today many other means of communication exist, including instant messengers like Skype. On average, we send around 120 emails per day—and many more messages are transmitted via messengers.
Trojan.Gapz.17 and Trojan.SkypeSpam.11 use contact information from Skype, Windows Messenger, QIP, Google Talk, and Digsby to send messages for the purpose of creating a botnet.
BackDoor.IRC.NgrBot.146 spreads via Skype messages. The malware connects the machines it compromises into a botnet, steals passwords, generates clicks, encrypts files, and demands a ransom—a jack-of-all-trades, indeed!
The Anti-virus Times recommends
Close unused ports in your system. It is very unlikely that any of your applications will need port 25—the most well-known malicious programs have used it to send email. To further complicate an intruder’s efforts, you can also change the standard port settings of your mail client.
To learn how to do it, please, refer to the issues Open windows and Come on in—the door’s open.
- Disable remote content in emails. Colourful advertising messages won't look as beautiful, but opening emails will become safer.
- Install updates—if you don't do this, attackers will exploit vulnerabilities to penetrate your system. They are still taking advantage of loopholes that were discovered a decade ago!
Important! Don't think that by installing all available updates you will solve the loophole problem completely. Alas, there are always unknown vulnerabilities. That's why messages should be checked before they are received by a client program. Dr.Web SpIDer Mail performs this task in Dr.Web Security Space. Using only an anti-virus module integrated with a mail client increases the probability that attackers will exploit a vulnerability—a message is processed before the anti-virus can check it.
A built-in anti-virus module will provide proper security only if the client communicates with a server via MAPI—the proprietary protocol from Microsoft. Messages transmitted via MAPI can't be processed outside the mail client. Dr.Web Outlook Plugin performs this task in Dr.Web Security Space. You can find out which protocols are being used by checking your email account settings.
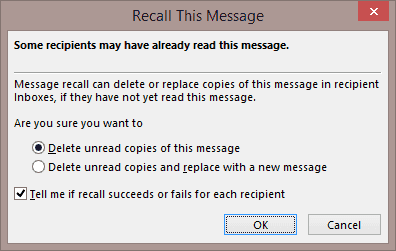
But what will you do if an acquaintance of yours is surprised to discover that some emails they get from you contain malware? Of course, you will start an anti-virus scan and contact technical support. However, you can save your reputation in other ways—you can recall the message. For example, Microsoft Outlook provides the Recall this message or Message recall option. It is available in Microsoft Outlook 2003 and later.
Naturally, to use this feature, you need to take a few extra steps. But, as the saying goes, “in fair weather, prepare for foul”; it’s always a good idea to have as many defences in place as possible so that when malware strikes, you will be able to keep your reputation intact.


![Shared 15 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
vasvet
06:22:48 2018-07-21