Come on in—the door’s open
Friday, August 5, 2016
Software developers think of today’s operating systems and applications as something akin to Swiss Army knives. Their impressive array of features enables them to perform virtually all common tasks. Meanwhile, these same developers don’t know exactly what users will be doing with their products. That’s why with default installations users never need to configure anything. The fact that manufacturers are focused on users en masse complicates the situation, and that’s why, as a rule, installation programs don’t give users any way to fine-tune the programs they’ve installed. What’s the result?
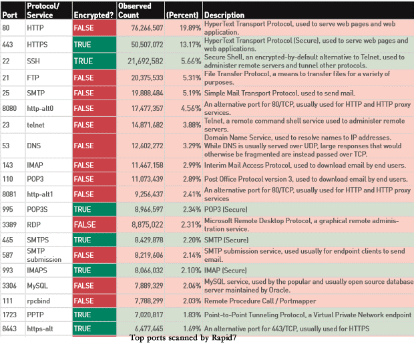
Rapid7 researchers scanned millions of servers across the Internet to try to discover potentially dangerous services that can transmit potentially important information unencrypted and should not be accessible from the Internet.
Hosts were scanned to detect which of the 30 most popular TCP ports were open.
The TOP 20 of the 30 scanned ports:
And these are only the 30 most commonly used ports.
According to the researchers, most applications do not use encryption to transmit data over the Internet even if they have the ability to do so.
Based on the scanning results, the researchers established the National Exposure Index and published statistics for every country in the world. In Russia (which ranked 11th) they discovered 2,832,044 devices of interest to hackers—these devices listen to all 30 TCP ports.
The researchers also found 11.2 million servers that provide direct access to their relational databases. Their scanner detected 7.8 million MySQL servers (port 3306) and 3.4 million hosts running Microsoft SQL Server (port 1433). While scanning DBMSs, the researchers didn't check the ports that PostgreSQL and OracleDB use by default.
The Anti-virus Times recommends
Once you’ve deployed all necessary applications on your server, disable all unused services and close all unused ports.
For example, a remote installation service can be useful at the deployment stage, but running the service after all the software is installed can pose a security risk.
You can use special applications to determine which ports are being used.
Dr.Web Security Space users do not need applications of this kind because Dr.Web offers them the following feature:
Click on the icon  in the system tray.
in the system tray.
Click on the padlock icon  to unlock access to the application's settings (this icon will now look like this:
to unlock access to the application's settings (this icon will now look like this:  ).
).
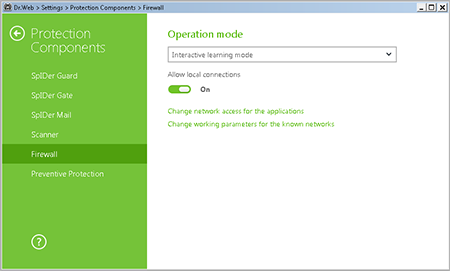
Click on the gear icon  , and in the Protection components menu, select Firewall.
, and in the Protection components menu, select Firewall.
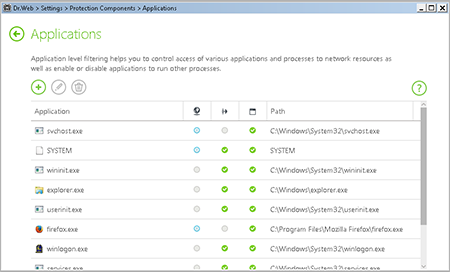
Select Change network access for applications. In the newly appeared window, you will see the list of running applications.
Click on the application you need.
In the next newly appeared window, you will see all the necessary information about the program.
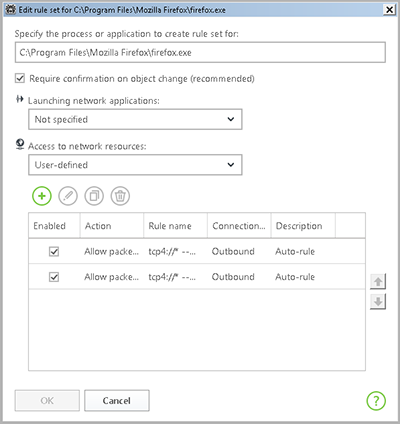
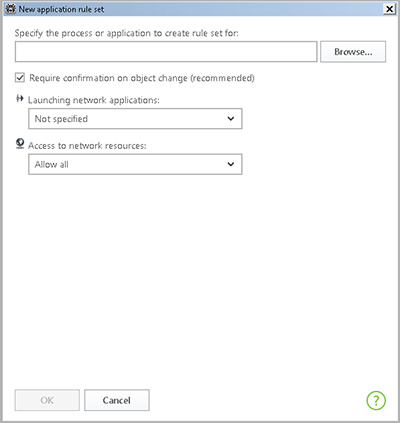
You can change the rule type, and create a list by adding new or editing existing filtering rules, and by changing the order in which they are executed. The rules are applied consistently, according to the list.
Several parameters can be defined for each application.
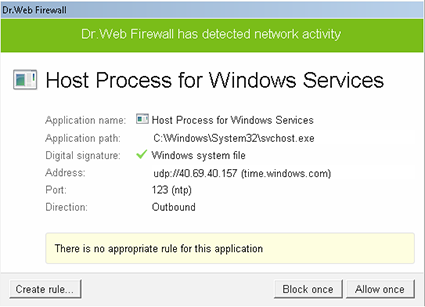
Naturally, some applications do not run all the time. Switch the Firewall to interactive mode, and whenever you start an application for which no Internet access rule is available, you’ll see this dialogue box:
Caution: Applications often access a large number of sites and nodes, and access permissions should be defined for all of them.


![Shared 15 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
vasvet
19:23:31 2018-07-02