Lots of loopholes
Monday, August 29, 2016
Plenty has been written about vulnerabilities, and about noble hackers infiltrating the computers of evil-doers, and vicious criminals gaining access to our computers.
According to the company Secunia, which collected information from about 20,000 PCs, 98% of machines connected to the Internet are using insecure software applications (applications for which updates have been released in order to close vulnerabilities). Here is the percentage of machines by the number of issues identified:
- 0 — 1.91% of PCs;
- 1-5 — 30.27% of PCs;
- 6-10 — 25.07% of PCs;
- 11 and more insecure programs — 45.76% of PCs.
Naturally, we’d all like to think that our computers are secure and impregnable to attacks. But is that really so? Of course, few of us can afford to hire a penetration test team. However, everyone can use specialised software. You can use a vulnerability scanner to determine whether loopholes are present in your system. Quite a few of them are available, both paid and free.
If you use Windows, you can use the free application Baseline Security Analyzer from Microsoft. You can get it here: https://www.microsoft.com/en-us/download/details.aspx?id=7558. To download it, you need to select a preferred language and system platform (32- or 64-bit).
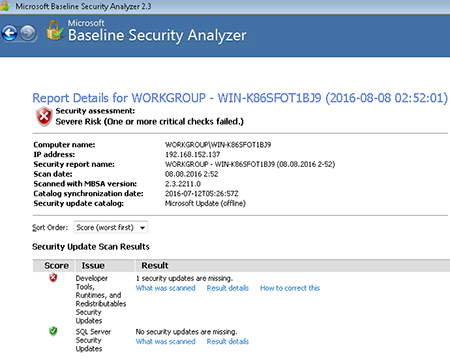
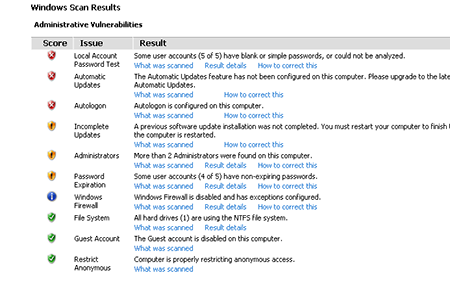
After installing it, you’ll see a shortcut to Microsoft Baseline Security Analyzer 2.3 appear on your desktop. After launching the program, you’ll need to specify that you want to scan a local host. The scan results can be rather depressing:
Press the corresponding buttons to receive more information or to learn how to fix the problems.
The Anti-virus Times recommends
One should never rest on one’s laurels. An increase in computer performance and special new research is leading us to realise that things that seemed safe till now (and were highly invested in) may in fact be vulnerable.
US Department of Defense (DoD) specialists can't check F-35 maintenance records because a Lockheed Martin database containing the necessary information doesn't meet DoD security standards, and testing of the combat fighter is being postponed for at least a year.
During each of their audits, DoD agents discovered machines running outdated operating system versions or software that was improperly configured. Furthermore, users were often found to have exposed their authentication credentials.
The audit team recommended that the DoD decrease the number of privileged user accounts, increase training, and appoint an executive agent to oversee cyber operations.


![Shared 15 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
vasvet
19:16:30 2018-07-02