I didn't sign up for this!
Monday, August 22, 2016
I just added $10 to my mobile account yesterday, and I'm out of money already! Perhaps, you can relate. Unfortunately, most of us only make a mental note of the fact that money is disappearing from our account; we don’t stop to think that, since this is happening to us, it must be because someone wants it to.
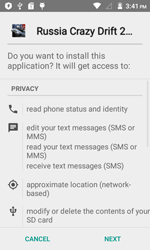
Android.MKcap.1.origin was used by fraudsters to sign up users to various paid services. A command and control server would send Android.MKcap.1.origin Android.MKcap.1.origin a link to a web page featuring premium content. After that, the malware would upload a verification code image from the page to a CAPTCHA-solving service. . As soon as the image-recognition procedure was complete, the Trojan would automatically send the result to the premium-content site to finish the registration process. If additional SMS messages containing confirmation codes were sent to confirm a subscription, Android.MKcap.1.origin would process them automatically as well and transmit the necessary codes to the site.
"Just install our malware, and you’ll be subscribed to lots of popular (in certain circles) services without lifting a finger!" makes for a good marketing campaign slogan, right?
By bypassing CAPTCHA, automatic SMS parsing, criminals can sign up users to as many services as they like.
Trojan.Ormes.186 can supposedly emulate clicks on a web page to confirm a subscription. Furthermore, if one visits sites such as YouTube or Facebook, Trojan.Ormes.186 downloads and executes a script that redirects the user to various file-sharing sites that profit from paid subscriptions.
Other Trojan.Ormes.186 features include the ability to log onto the online casino sites that appear on its hardcoded list.
If the site offers users the opportunity to install applications for social media, the Trojan will automatically redirect the user to the corresponding download page. Once these web pages are open, Trojan.Ormes.186 emulates a mouse click on the link indicating one’s agreement to the installation—as a result, the application is installed without user consent.
http://news.drweb.com/show/?c=5&i=9533&lng=ru
Furthermore, Trojan.Ormes.186 displays ads and is able to independently “like” whatever sites interest it!
On Facebook, it injects a hidden iframe into web pages (to adjust the values of certain variables required for the Trojan's operation). By doing this, Trojan.Ormes.186 can automatically place ‘Like’ on a number of websites that appear on a special list.
The Anti-virus Times recommends
To make services as user-friendly as possible, routines that were previously performed by humans are now automated, which is both fortunate and perilous. And criminals take advantage of this. If you suspect that your funds have been debited in a fraud scheme:
- Go to your personal account area on your mobile carrier's website and request your usage statistics for the past few months.
- Contact the carrier's support service, and find out what chargeable content services you've been subscribed to, when it happened, and what numbers are involved. If the services were enabled without your consent and you didn't confirm the subscriptions and received no SMS confirmations, explain this to the support staff. Should they claim that you have confirmed the subscriptions, request a billing report that will contain information about all the incidents involving the short messages.
- Regularly review reports about any business conducted with your mobile account—this will help you determine whether you've been subscribed to services without your consent.
- Try to find out more about the content provider affiliated with the fraudsters.


![Shared 15 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
vasvet
04:35:44 2018-07-06