Burying your head in the sand won't save you from extortionists
Monday, August 1, 2016
The Tewksbury Police Department (Massachusetts, USA) found itself in an embarrassing situation. All the working files on the department's computers were encrypted by an unknown application. To get the decryption key, the police were told they would have to pay $500 in bitcoins.
When the Tewksbury police’s computers began having performance issues, their employees were having difficulty accessing criminal records; no one suspected anything was wrong. They thought it was just the usual system crankiness. No big deal, said the Boston Globe.
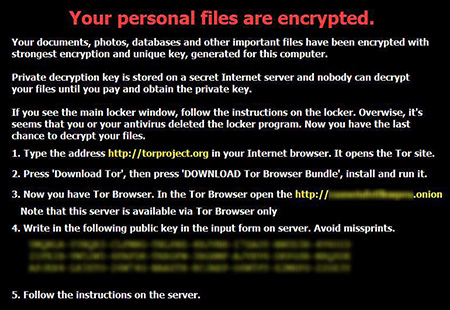
The truth was revealed when the ransom demand appeared on their screens: "“Your personal files are encrypted. File decryption costs ~ $500. If you really value your data, then we suggest you do not waste valuable time searching for other solutions because they do not exist."
The police summoned a technician who confirmed that indeed there was no other solution. State and federal law enforcement agencies, as well as experts from two private Internet security companies, joined the efforts to solve the problem. But no one was able to unscramble the files. After five days, the Tewksbury police transferred the required sum to the account specified.
“My initial thoughts were that we were infected by some sort of a virus,” Tewksbury Police Chief Timothy Sheehan recalled about the December 8 attack. “Then we determined it was a little bit bigger than that. It was more like cyberterrorism.”
Apparently, the police chief didn't understand a thing about what had happened. And he is not the only one who doesn't understand modern threats and the ways people can protect against them. Here are some comments left on another site about the incident.
Hmm. That sounds scary.
Hey guys, what should I read on information security?
I'm a programmer, but system administration isn't really my thing. But now I have to manage our family’s network (about a dozen machines). How should I organise my network so that if one computer gets infected, the shared network drives do not pop off? Is there any good stuff to read on the subject?
We won't be quoting any of the replies here, but, alas, most of them also indicate low competence when it comes to protecting computers from today’s threats. What is the cost of this?
A research project conducted by Kent University (Great Britain) showed that around 41% of victims pay the ransom.
Although there are heroes like Gary Bowen from the Police Department in Collinsville (Alaska). In June 2014, he refused to cooperate with "terrorists" and never paid the $500 ransom. The files compromised in his department were never recovered.
After reading news stories like this, companies surrender instantly. What they need to do is to start taking care of the security of their information: to learn how to protect their systems from encryption ransomware, restrict access permissions, and make back-ups…
But instead:
Today, one in three companies has a reserve account containing cryptocurrency (usually bitcoins) that is to be used in case of cyber-attack.
Research shows that companies are willing to pay up to 50,000 pounds ($72,700) to unlock their machines and get back their intellectual property.
Medium-sized companies, those companies with 501-1,000 employees, are more likely to cut a deal with criminals (57%) . Small businesses (250-500 employees) are less willing to pay: only 36% are prepared to pay ransom. Major market players, i.e., companies employing more than 2,000 people, have turned out to be the most "stubborn": only 18% of them are prepared to pay.
At the same time, 48% of the respondents admitted that their company does not make daily backups. So, in the event of a ransomware attack, they will find themselves in a very difficult position.
Do you think these measures will save people who want to bury their heads in the sand?
Even if, before they attack, hackers don't know how much money a company’s or user’s account holds (they don’t always succeed in infecting an accounting department computer to determine a company’s account balance, and only then encrypt that company’s files and demand a ransom), the “ostriches” leave themselves at the mercy of “hunters” anyway!
Encryption programs check the bitcoin wallet file for “wallet.dat” on the target computer. After that, the attackers set a ransom based on the amount of money available to the user. If they also learn you have backups, this can change the amount they demand.
The following materials were used in the creation of this article:
https://nakedsecurity.sophos.com/2016/02/17/locky-ransomware-what-you-need-to-know/
The Anti-virus Times recommends
- Don't keep all your eggs in one basket. Use different machines to surf the web, carry out transactions, and store important documents.
- Create backups and store them in locations that will be inaccessible to encryption ransomware—use protected storage or another computer. Remember that a hacker can monitor your actions and wait until you access secure data storage.
- Disable launching executable email attachments.
- Restrict access permissions for your PC or handheld.
May your data stay safe with you—always!


![Shared 15 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
vasvet
21:02:50 2018-07-19