A virtual myth
Wednesday, July 27, 2016
A virtual (or on-screen) keyboard enables users to enter characters on the screen of a PC, tablet or smart phone. Depending on the device type and model and the features of the keyboard software, text can be entered by clicking on virtual keys with a mouse or tapping on them with a finger or stylus.
It is believed that using an on-screen keyboard to work with confidential information—bank accounts, personal information, and logins and passwords—will prevent the information from being recorded by keyloggers and relayed to criminals.
However, the problem is that criminals know about virtual keyboards, too, and the fact that users think they’re secure.
Linux.BackDoor.Xunpes.1 can execute over 40 commands, some of which involve keystroke logging and taking screenshots.
The banking malware Trojan.PWS.Panda can take screenshots of the area around a mouse cursor as each click is made. Thus, if a user makes a click (e.g., on the on-screen keyboard), the screenshot taken at that moment will display that area of the screen (and the criminals will see which keys were being pressed).
When it comes to Android, where an on-screen keyboard is a standard means of input, the number of Trojans carrying similar payloads is even greater. Some Trojans take screenshots upon command, while others take them when certain conditions are met. For example, when a user launches a banking application or fills out forms (at the moment an on-screen form becomes active). Android.Backdoor Trojans (Android.Backdoor.260.origin, Android.Backdoor.174.origin) are a good example of malware that engages in this activity. Many banking and spying Trojans can also do this.
Obviously a virtual keyboard doesn't guarantee secure input on a site that has been compromised or if a user has ended up on a bogus site as a result of a phishing attack. Does it matter what method you use to enter your password if the input will be instantly relayed to criminals?
The Anti-virus Times recommends
- Learn more about phishing attacks and how to avoid them here. Because entering data on a phishing site almost certainly results in a loss of money, account access, or other valuable information, it is very important to recognize the danger in time.
- When entering data in forms on various sites, stay vigilant. Make sure you've ended up on the site that you actually intended to visit.
- Do not disable the SpIDer Gate HTTP monitor in Dr.Web Security Space. The monitor uses a database of non-recommended sites and will prevent you from accidentally visiting them.
- Don’t rely on the existence of some “miracle cure” to solve all your problems.
"I wasn’t protected from keyloggers when I was typing in Notepad, no matter what mode I was in—even paranoid ".
An unknown user
A proactive defence provides the best protection. Even an unknown malicious program should not be able to start up in your system. The operating system provides a means to restrict access.
Dr.Web Security Space can do this, too
Right-click on the icon  in the system tray; click on the padlock icon
in the system tray; click on the padlock icon  to enable access to the program's settings (the icon will now look like this:
to enable access to the program's settings (the icon will now look like this:  ). After that, press the gear icon
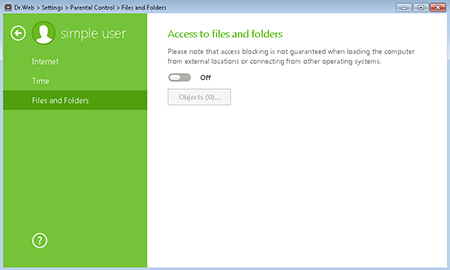
). After that, press the gear icon  . In the menu, select Parental (Office) Control. In the subsequent window, select the user account for which you want to change permissions, and in the Files and folders section, click Change. In the window that opens, click Objects.
. In the menu, select Parental (Office) Control. In the subsequent window, select the user account for which you want to change permissions, and in the Files and folders section, click Change. In the window that opens, click Objects.
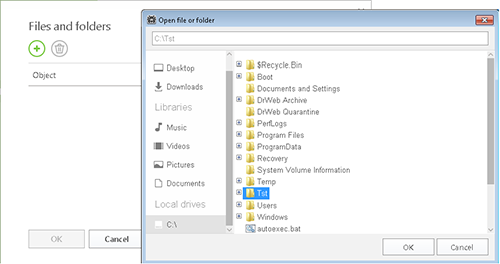
Press  . Now select the files and folders you want to block access to, and press ОК.
. Now select the files and folders you want to block access to, and press ОК.


![Shared 15 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
ka_s
06:42:41 2020-08-25
razgen
22:21:14 2018-09-16
vasvet
10:59:05 2018-07-04