Crime is served. Enjoy!
Friday, July 1, 2016
To rob individuals and companies of their money more effectively, cybercriminals not only design new sophisticated technologies but also adopt modern business techniques.
For example, in addition to selling Trojans (or their modules) on underground forums, they lease the infrastructure that allows Trojans to be used to steal data and money.
Under the crime-as-a-service (CaaS) model, customers are provided not only with malware but also with an out-of-the-box solution to control Trojans and collect statistics. Lone attackers and organised criminal groups are among the customers of "crime providers".
For example, to control a botnet consisting of nodes infected with Android.ZBot.1.origin, criminals have designed and lease an administration panel. Access to the panel is granted for a certain period whenever a client pays for it. In other words, the administration panel is provided as a service on a subscription basis.
The Trojan “admin panel” connects to control servers maintained by the CaaS provider—the licensor. Criminals can set up any number of command and control servers and design any number of admin panels to offer a malware control service. Criminals use the panels to send commands to Trojans. Trojans communicating with different command and control servers comprise independent subnets of the botnet.
Every Android.ZBot.1.origin subnet incorporates thousands of compromised smart phones and handhelds.
What can the panel’s licensees steal from infected zombie devices?
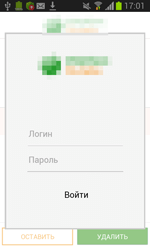
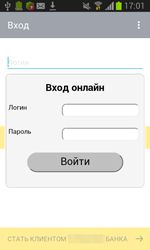
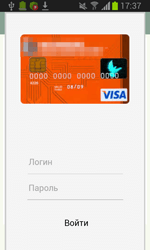
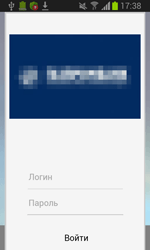
From devices infected with this particular Trojan, they can acquire online banking logins and passwords. A fake authorisation dialogue is used for this purpose. So the victims themselves are providing CaaS subscribers with their online banking access information.
Subscribers are offered a lot of options including various fake authorisation dialogues that imitate banking software from various banks. Furthermore, clients can come up with a design of their own. An attacker commands the Trojan to stand by until the banking application they’ve specified has been launched on the infected device. And if that happens, the Trojan will download a fake authorisation dialogue from a command and control server and display it.
The Anti-virus Times recommends
- Modern malicious programs are sophisticated money extractors. If necessary, they can download from a server various modules that have been crafted by criminals or purchased on underground forums.
- All Anti-virus Times readers should give advance thought to the security of their handhelds. Unfortunately, modern malware can reside in a protected system area. In situations of this kind, only Dr.Web Security Space can help—free Dr.Web Anti-virus for Android software can't neutralise sophisticated threats. To find out why, read the issue A fish rots from the head down, and a smartphone from the root.


![Shared 16 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
vasvet
16:36:36 2018-07-15