Evil script writers: How to avoid their villainous output
Wednesday, October 17, 2018
What are scripts and what makes them special? Let's compare the contents of a binary file and that of a script.
On the left, you can see what's inside the Windows Explorer's file, and on the right, the contents of a randomly selected script downloaded by our browser when a webpage was loading. The difference is quite obvious. A binary file can be launched right away—it contains machine code that only your computer's CPU will understand. Under normal circumstances, no other software is required to run an executable. But a script is different. It can’t execute itself. Another application has to do that for it.
A script is akin to the scripts used for films or plays.
ACT I
SCENE 1
Elsinore. A platform before the castle.
Francisco at his post. Enter to him Bernardo.
Bernardo
Who's there?
Francisco
Nay, answer me. Stand and unfold yourself.
A script is just text. A director and actors turn it into action.
Computer scripts are no different. They define actions that must be performed. To accomplish this, an interpreter—a program that executes scripts—is required.
This is interesting. Here we’ve provided a somewhat simplified definition of a script. Some scripts are actually compiled. A myriad of other script formats exist too. It’s funny that it really is simpler to open a file to see whether or not it contains text. Using another program to do this is much more difficult!
- For example, let's assume that we get hold of a random file. Now we need to write a program that will be able to distinguish between binary and text files. Has anyone invented a way to do this?
- One can’t say this with 100% certainty, but no text file is ever going to contain symbols such as #0.
Why are scripts dangerous?
It is not the malicious impact they can have that presents the biggest problem. Encryption ransomware species can be implemented as binaries as well as scripts. But binary files are "tightly packed", and their contents is structured in a certain way. That's why signatures enable anti-viruses to identify them easily and with a high degree of accuracy.
Making even small alterations to a binary file's contents (e.g., adding a couple of whitespace characters to the code) may render the file non-operational. Meanwhile, malicious scripts can't be crippled so easily.
Does this code possess any peculiar feature that we can use to generate a signature? Well, it's just a piece of code that doesn't appear to be particularly frightening.
A malicious script may contain no malicious code whatsoever. For example, encryption ransomware may rely entirely on the features of an operating system that already incorporates all the programs necessary to accomplish the malicious task—one just needs to run them.
We looked through the sequence of commands and realised why the anti-virus wasn't triggered by the script's execution.
Once the script's execution commences, encryption software is downloaded from the attackers' site. The software is a legitimate PGP encryption utility. Then the script initiates data encryption.
So the anti-virus doesn't regard the routine as malicious and assumes that the actions are actually being performed by the user who has just decided to protect their documents.
Therefore, malicious scripts are dangerous because:
| ✔ Generating signatures is complicated | ✔ Script signatures can easily be altered | ✔ Malicious actions look like legitimate user actions! |
| For a signature to be truly unique, it may have to be extremely long. | There exist special services that enable attackers to determine which malware signatures will trigger anti-viruses. | From an anti-virus's standpoint |
Why do cybercriminals like scripts?
In addition to the aforementioned advantages, another factor stands in favour of scripts: a script can be run on a variety of platforms, which is not possible for binary files. Scripts only describe what needs to be done.
Doctor Web security researchers registered the first attacks of this Linux.LuaBot family Trojan in December 2016. All versions of this Trojan are written in the Lua script language.
Linux.LuaBot is a set of 31 Lua scripts and two additional modules, each of which performs its own functions.
The Trojan infects devices possessing the following architectures: Intel x86 (and Intel x86_64), MIPS, MIPSEL, Power PC, ARM, SPARC, SH4, and M68k—in other words, not only computers, but also a wide array of routers, set-top boxes, network storages, IP cameras, and other “smart” devices.
Do any dangerous script-based malware species exist?
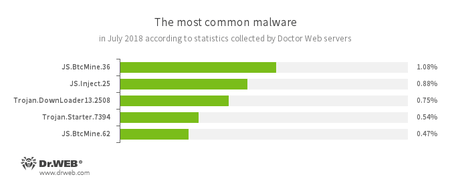
There are more than enough of those. Here is a recent example from Doctor Web's news posts:
- JS.BtcMine
- Pieces of JavaScript code used for covert mining.
- JS.Inject
- Pieces of malicious JavaScript code. They inject malicious scripts into webpages
Today's most common malicious species are script-based!
This is interesting. You don’t run across viruses, malicious programs that infect other files, among scripts. But Trojans and worms – you see lots of those. For example, JS.Faceworm.1 is a JavaScript-based worm spreading via Facebook. Trojan.Encoder.4860 is an encryption ransomware script, which is also known as JS.Crypt. All its code is written in the JScript language.
#scriptHeuristic #Trojan #security #script #Dr.Web_technologies #malware
The Anti-virus Times recommends
Is there a way to protect a system from malicious scripts? Certainly.
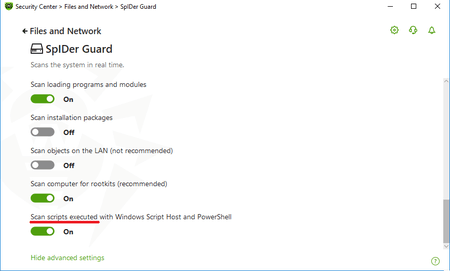
We’ve already mentioned that behavioural analysis for scripts is prone to error. However, machine learning can be used to generate rules that predict the behaviour of malicious scripts. This feature has been incorporated into Dr.Web solutions, starting with Dr.Web Security Space 11.5 and Dr.Web Enterprise Security Suite 11.0.
The feature complements the ScriptHeuristic technology, which prevents malicious scripts in browsers and PDF viewers from being executed.
ScriptHeuristic
- It prevents any malicious browser scripts and PDF documents from being executed, without disabling the functionality of legitimate scripts.
- It protects against infection by unknown viruses that try to access systems via web browsers.
- It works independently of the Dr.Web virus databases, in any web browser.
Computers can be protected from malicious scripts—you just need to pick the right security tools to do it!



![Shared 0 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
razgen
00:00:15 2018-10-18
Неуёмный Обыватель
08:34:30 2018-10-17
vasvet
05:32:18 2018-10-17