Firmly rooted
Friday, June 1, 2018
Doctor Web’s researchers have detected malware in the firmware of Android devices on numerous occasions. Sometimes these Trojans behave rather cunningly. For example, to make sure that a device owner doesn't suspect anything, they may wait a few months before springing into action. And, on some occasions, removing the Trojan is not an option because doing so can turn the smart phone into a useless "brick".
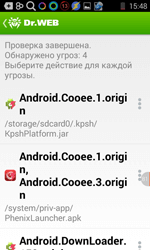
In the case of Phillips s307, a pre-installed Trojan resides in the device's firmware—Android.Cooee.1 is incorporated into the launcher that facilitates the operating system's boot-up process. That's why performing a factory reset won’t remove the malware from a device. Therefore, before the malware can be removed, another program must be installed and set as the default launcher.
How can a Trojan end up in a device's firmware?
- Buying a device that has already been compromised is one way. In this case the malware gets onto the device as soon the device manufacturer or a service company uploads the firmware to it.
Firmware can also get infected later—after the manufacturer has discontinued support for a device.
- Manufacturers often find it commercially inexpedient to supply obsolete devices with Android updates indefinitely, and sometimes it may even become technically infeasible for them to do so. This applies both to the manufacturers who sell devices under their own brands and to those ordering devices from other manufacturers and then marketing them under their own trademarks. The latter can delegate device maintenance and support services to other parties. In this case, a device may receive an update that will change the system settings so that another company will be able to support it (e.g., one that changes the address to which information will be sent when necessary). There is nothing wrong about that.
- At the same time, users usually don't buy new devices just to get a new version of the operating system—after all, they think, why care about a new OS version if their device is working properly under an obsolete OS?
- Virus makers find it lucrative to exploit known vulnerabilities in earlier operating system versions; their malware programs can gain root privileges and copy themselves or other Trojans into otherwise protected areas. As a rule, opting for a factory reset helps cure a device, but sometimes, in particularly complicated cases, a device needs to be re-flashed since Trojans can persist in the system even after a factory reset.
However, we are not going to develop conspiracy theories of our own. It is very unlikely that device manufacturers collude with virus makers.
Manufacturers and brand owners are on equal footing with ordinary users when it comes to falling victim to unscrupulous resellers and cybercriminals.
The presence of Trojans in firmware most likely indicates that manufacturers don’t yet grasp the magnitude of the problem. They’re probably not scanning their firmware before it gets uploaded to smart phones, or they’re not inspecting it well enough. Do manufacturers have the technical capabilities and sufficiently qualified specialists to do that? Do they deem it necessary? We'll leave these questions for the device makers to answer.
How do Trojans sneak into official firmware and updates?
Every new Android version is compiled by the respective device manufacturers. They incorporate into their firmware their own UI and software as well as software from other parties that is popular in the region in which the devices will be marketed. They strive to outfit their products with as many useful programs as possible to gain an edge over their competitors. However, no manufacturer can design and develop all of their programs on their own, which is why they also select software from third-party developers. And this is where cybercriminals can come into play: an unscrupulous developer can incorporate something into their program that no one will know about.
These are the most common scenarios showing how Trojans can find their way into firmware:
- Software from an unscrupulous developer is uploaded to a device, or the developer is quite trustworthy, but it employs a programmer who has a hidden agenda.
- Virus makers can gain access to a developer's infrastructure and covertly deploy malicious code in the firmware.
- A compromised SDK (software development kit).
- A cybercrime ring acquires a shipment of devices and re-flashes them with compromised firmware. Then the infected devices find their way onto the market.
Developers who get caught red-handed implementing malicious features in their software usually call it a misunderstanding. They claim that a feature regarded by security researchers as malicious is in fact very necessary, handy, and in no way dangerous.
- For example, when it was discovered that a piece of software was sending user text messages and call logs to Chinese servers, the smart phone manufacturer BLU claimed that this was being done solely for the purpose of fighting spam.
- Meanwhile the developers behind the SDK that Dr.Web classifies as Android.Gmobi. 1 stated that they implemented a feature that enables users to do whatever they please on their devices in order to help users save money and that there was no danger in this whatsoever.
However, all these incidents have one thing in common: whenever security researchers discovered a potentially dangerous feature, the respective developers removed it from their products.
The Anti-virus Times recommends
- You mustn’t blindly trust anyone. Alas, many users try to speed up anti-virus scans by restricting them to files being downloaded and disabling the file monitor. However, as we've already shown, a Trojan can reside on a device from the very beginning or arrive with an official update after a device has been purchased. That's why regular full device scans are an absolute necessity.
An anti-virus can't know all the malicious programs in existence. It may happen that a brand-new Trojan, one virus analysts don’t yet know about, sneaks onto a device via an update. In such cases. Dr.Web Security Space for Android users can send the Trojan to our laboratory for analysis.
To do this, take the following actions:
Tap and hold the file in question; then tap Send to laboratory.
- If you want to receive feedback from our virus analysts, in the next dialogue, enter your email address.
Select one of the categories for your query:
- Suspected file — if you believe that the file poses a threat.
- False positive or False positive by Origins Tracing — if you think the file was incorrectly classified as malware.
Use the file name to determine which of the false positive categories you need to choose. If the filename has the ".origin" suffix, then select False positive by Origins Tracing. In all other cases, choose False positive.


![Shared 0 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
Неуёмный Обыватель
02:01:59 2018-07-30
vasvet
17:02:20 2018-06-16