Wolves in sheep’s clothing lurk in stores
Monday, June 20, 2016
Compared with other download sources, mobile application stores are deemed to be the most secure for users. Indeed, popular stores try to prevent malware from penetrating their websites by scanning vendor installation packages. As a result, the risk of getting infected with a Trojan is far less than on any file sharing site; it’s no coincidence that those sites are referred to as “scrap heaps”.
Unfortunately, only a pathologist can give a full warranty―and, in this case, the “pathologist” is the employee at the service center to which you bring your infected mobile device for cross-flashing or the virus analyst helping to investigate how your device got infected.
How is it that users can download Trojans even from Google Play? The reasons are many.
- Virus writing is a business. Day in and day out, cybercriminals are grinding out Trojans. It’s likely that the store administrations simply don’t have enough qualified specialists on staff to thoroughly check all the applications.
- Mobile applications are enormously abundant, and many of them are free of charge. Cybercriminals just take an application, modify it, add malicious features, and locate it in the applications catalogue. They mark it as “free” so that users who maniacally keep tabs on new, free applications immediately download it—particularly, if it’s a game.
- Cybercriminals can have inside knowledge of what anti-virus is being used to scan applications, allowing them to test their applications in advance to see whether they can bypass detection.
- Cybercriminals can design their malicious programs to remain inactive for a certain period of time after they’ve been installed or while they’re being tested under certain conditions. Programs determined by testing to be potentially dangerous are a dime a dozen.
- Sometimes malicious code can be absent in a program located in a store. Most Trojans install additional malware only after they penetrate a system…
And this list is far from complete.
And what do you think? Why do users download infected applications from Google Play so often?
The Anti-virus Times recommends
- Do not implicitly trust reviews on an application page. Unfortunately, program ratings can be promoted (you can find information on how this happens in the Anti-virus Times issue “The epoch of “fakes”), and all the materials promoting a program may have been generated by cybercriminals.
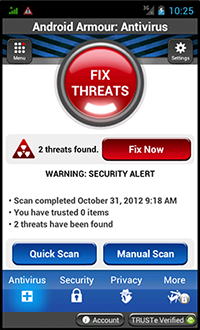
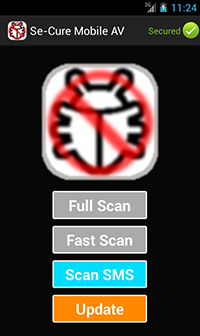
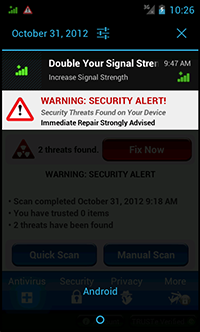
- The first program to be installed on a PC or a mobile device should always be an anti-virus. And, if possible, it should be downloaded from the vendor’s official website. Cybercriminals have created and will continue to create fake anti-viruses—programs that act like anti-viruses (according to the Dr.Web classification system, all Android malware belongs to the Android.Fakealert). For example, Android.Fakealert.10.origin is distributed as a viewer for adult video clips. Once launched, this malicious program mimics the look and feel of a legitimate anti-virus and prompts users to scan their mobile device for viruses. It offers to neutralise whatever threats are detected if the user purchases the “full version” of the program.


![Shared 17 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
razgen
22:26:08 2018-09-15
vasvet
14:26:04 2018-07-24