About miners and their output
Monday, March 5, 2018
It's no secret that modern office computers have more than enough power to carry out their daily routines. And server capacity is often underutilised, too, because a server’s hardware configuration is intended to bear a maximum load, which may be three to five times higher than average.
As a result, machines of this kind allow for a number of tasks to be performed silently so that users remain completely unaware of them unless a program running in the background gets particularly "greedy".
I noticed yesterday that the GPU load spiked to 98%-99% while my machine was lying idle. I did some searching about the issue and realised that my video adapter is being harnessed for mining. There are lots of forum topics about how to make a profit from this activity, what hardware to use, and stuff like that. But I found no instructions on how to rid a system of this “freeloader”. The graphic card gets rather noisy under load, which makes me feel uncomfortable, and the very idea that someone is making money off of me infuriates me. Please, tell me, is there something I can do about this?
Mining is a way to acquire modern digital currencies, with bitcoin being the most famous of them. Mining requires high-performance hardware, and criminals believe they can "borrow" it from ordinary users by infecting their systems with the corresponding malware.
The first malicious program of this kind was discovered quite a while ago—on July 7, 2011.
To date, several malicious programs are known to mine Bitcoin. They include Trojan.Coinbit and certain Trojan.Vkbase species. A new Trojan horse, Trojan.BtcMine.1, uses two legitimate mining programs to utilise the resources of a victim's computer.
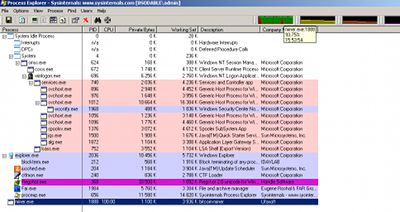
The screenshot shows information about the load placed on the CPU when the miner software, launched by Trojan.BtcMine.1, is running in the system.
The review text we've just quoted highlights two interesting facts:
- The mining application doesn't behave like a polite guest but rather consumes as much of the CPU capacity as it can get.
- The Trojan uses legitimate mining software. This means that even if nothing in your system points to malicious activities of any kind, but unknown processes appear to be running, it can nonetheless indicate that your system has been compromised, and that means your security software should respond when programs that could be used by attackers emerge.
How do malicious mining programs spread?
Designed to mine Litecoins, Trojan.BtcMine.221 spreads in the guise of various applications and browser extensions—for example, one of them supposedly helps users find lower priced goods online.
The program's developers claim that the extension, called Shopping Suggestion, automatically acquires information about the goods users are viewing in their browsers and searches the Internet for the same goods at lower prices. Furthermore, this Trojan is often disguised as other applications such as the VLC player or software for anonymous surfing on the Internet.
Digital signatures are believed to serve as anti-virus security alternatives. Developers must sign their applications to confirm their legitimacy. A sensible idea, but…
It should be noted that the digital signatures were obtained by the developers for legitimate applications with similar names, but Trojan.BtcMine.221 has the signature too.
So if the security of a system were solely based on the verification of digital signatures, the Trojan could easily circumvent it.
Affiliate programmes are also used to infect computers with programs of this sort.
A repeat monitoring of installmonster.ru, an affiliate programme used to monetise file traffic, has reaffirmed how malicious it really is. In early December, it was facilitating the distribution of the file SmallWeatherSetup.exe, which supposedly would install a weather toolbar on user computers. Indeed, a legitimate, harmless application that displays up-to-date weather information and bears a similar name does exist. However, the file being promoted by installmonster.ru was bundled with the not-so-harmless Trojan.BtcMine.218.
Affiliate programmes for site owners may help them make some extra money by hosting certain applications on their websites. Affiliate programmes often initially indicate their not quite legitimate purpose.
By the way, in this case the weather widget would really get installed: the distribution file did incorporate this harmless application. But together with it was the Trojan…
If you download and install an application from a site that doesn't belong to its developer, you are your own worst enemy.
To criminals, legitimate mining applications aren't particularly convenient because users may notice them, which is not a good thing. That's why, in addition to legitimate programs, they use special software belonging to the Tool category. Under the Dr.Web classification system, programs of this kind are designated as Tool.BtcMine.
Mining software is available for all platforms.
In 2014, several mining Trojans for Linux, such as Linux.BtcMine and Linux.CpuMiner, were added to the virus databases as were similar applications for Android, including Android.CoinMine.1.origin and Android.CoinMine.2.origin. They were distributed along with popular legitimate programs that had been modified by attackers.
Mining often only provides criminals with additional income.
Trojan.Mods.10’s main purpose is to replace browser window content with webpages crafted by criminals, but criminals also equipped the program with a bitcoin mining module.
https://news.drweb.com/show/?c=5&i=4202&lng=en
Trojan.Tofsee, which is primarily designed to send out spam, can also download as many as 17 loadable plugins from remote servers. Implemented as dll files, the plugins include the bitcoin mining program dubbed Trojan.BtcMine.148.
Over time, the capacity of a single PC became insufficient for mining, and virus makers started producing real monsters.
Trojan.BtcMine.737 copies itself to the root folders of all the hard drives (this operation is repeated periodically) and goes through all the computers in network places, trying to connect to them by using logins and passwords from a special list. Moreover, the malware tries to crack the password to the Windows user account. If successful and provided that the necessary hardware is available, Trojan.BtcMine.737 sets up an open Wi-Fi hotspot.
If a connection is established to any computer on the network, the Trojan tries to replicate itself to that computer and run the copy using Windows Management Instrumentation (WMI) or Task Scheduler.
Because Trojan.BtcMine.737 can spread itself over a local network, it can pose a threat to computers that aren't protected by an anti-virus.
Interestingly, Trojan.BtcMine.737 is the fruit of the collaboration of multiple criminals. To mine bitcoins, it uses a utility from another developer—Dr.Web detects the program as a Tool.BtcMine species. The utility's author makes it available under the provision that they receive 2.5% of the total amount mined using the program.
Mining Trojan infection statistics are also noteworthy.
An average of 203,406 bots go online every day. As many as 49,149 newly infected machines connected to the network in just three days in December 2013, while the number of Trojans removed during the same period reached only 6,028.
Over 200,000 users downloaded a dubious, smart online shopping program!
And in conclusion, we can also offer some Dr.Web CureIt! statistics.
- Trojan.Zadved displays fake search results and fake pop-up messages from social networking sites.
- Trojan.BtcMine.793
- Trojan.DownLoader programs download other malware onto infected computers.
- Trojan.InstallCore.1903 is an unwanted and malicious software installer.
This is the program that may be ravaging your computers while you're reading the latest news post about encryption ransomware.
#mining #corporate_security #terminology #malware #TrojanThe Anti-virus Times recommends
The idea of utilising unused hardware capacity is not exactly a new one—just recall the search for extraterrestrial civilisations and grid computing for medical projects. But criminals are willing to take advantage of any honest endeavour.
The average daily income of criminals is 1,454.53 USD.
If every user installed Dr.Web, criminals wouldn't be able to line their pockets with this money.





![Shared 1 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
Неуёмный Обыватель
23:48:53 2018-07-27
vasvet
21:07:08 2018-06-28