Pointing fingers
Thursday, February 22, 2018
Every mistake has a first and last name.
A universal truth
When “everyone knows” that evil is only committed by Russian hackers, trying to convince people otherwise is useless—someone will continue to repeat that convenient explanation and take it for a fact. And those supposed hackers aren't necessarily Russian nationals. They can be any cybercriminal recruited by the Russian government.
For example, a number of Polish banks came under attack recently. Naturally, the attackers were identified almost instantly.
As part of the attack, the intruders infected a website belonging to the Polish Finance Oversight Commission (Komisja Nadzoru Finansowego, KNF). The infection remained unnoticed for over a week, during which time malicious code facilitated the deployment of remote access Trojans on the computers of those visiting the website.
Information about a failed attack on the infrastructure of the Polish Ministry of Foreign Affairs appeared in the Rzeczpospolita (a daily newspaper) on January 29, while the actual breach attempt occurred in December 2016.
The Ministry of Foreign Affairs and Prevenity are confident that the attack was carried out by the hacker group APT28, whose members are also known under the aliases Sofacy and Fancy Bear.
https://www.gazeta.ru/tech/2017/02/05/10506179/jeszcze_polska.shtml#page3
However, a subsequent investigation revealed some interesting details.
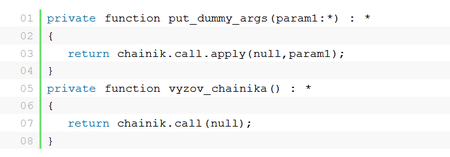
On February 20, 2017, BAE Systems expert Sergei Shevchenko presented a description of a recently discovered malicious program. The researcher indicated that the malware's code contained a large number of false flags meant to give the impression that the campaign was orchestrated by Russian-speaking hackers. However, Shevchenko noted that any Russian-speaking researcher would immediately expose the ruse because the criminals probably used Google Translate or something even less capable of speaking Russian.
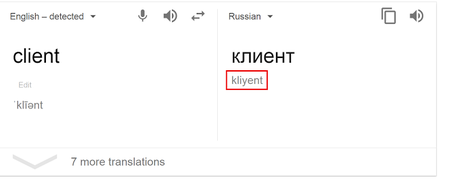
The researcher also provided some illustrative examples of the fakes he discovered in the code. The transliterated text was obviously machine-generated rather than produced by a human being. A native speaker of Russian is unlikely to spell выходить as vykhodit, клиент as kliyent or come up with something like kliyent2podklyuchit— obviously derived from client2connect.
The myth about all-powerful Russian hackers (note that hackers from China, North Korea, and other countries have seemingly disappeared), which has become quite topical recently, is based solely on claims made by certain information security experts. We’ve already discussed some of the claims made by experts of this kind. We don't know how far from the truth this myth is. But we're sure of one thing.
Based on its 25 years of continuous experience researching malware, Doctor Web can state with confidence that identifying the origins of a malicious file is a very difficult task.
Modern criminals aren't obliged to supplement their code with their signature and home address. Yesterday’s virus makers sought fame—today’s are only interested in money. Hacker groups are often multi-national and include citizens of countries that have bad relations with the state whose infrastructure they are attacking.
And this is the strange thing: despite the fact that Turkey and Russia do not get on very well, for some reason Turkey’s computers are being attacked by American hackers, rather than Russian ones.
According to Turkish Minute, Turkey’s Energy and Natural Resources Minister Berat Albayrak stated that the country's power supply network came under intense hacker attacks, supposedly from US soil.
He also noted that the recent power supply failures were caused by those very attacks.
https://www.gazeta.ru/business/news/2017/01/08/n_9535331.shtml
He also noted that the recent power supply failures were caused by those very attacks.
President Obama signed executive orders laying out how far military commanders around the globe can go in using cyberattacks and other computer-based operations against enemies and for routine espionage purposes in other countries.
The orders detail when the military must seek presidential approval for a specific cyber assault on an enemy and weave cyber capabilities into US war-fighting strategy.
https://habrahabr.ru/post/122448
Future capabilities must sustain our ability to defend the homeland and project military power globally. Important investments to counter A2/AD, space, cyber, and hybrid threats include: space and terrestrial-based indications and warning systems, integrated and resilient ISR platforms, strategic lift, long-range precision strike weapons, missile defense technologies, undersea systems, remotely operated vehicles and technologies, special operations forces, and the Cyber Mission Force, among others.
http://inosmi.ru/op_ed/20150703/228922858.html
According to NATO Secretary General Jens Stoltenberg, a massive cyberattack can trigger Article 5 of the North Atlantic treaty in the same way as a conventional military assault can.
http://www.newsru.com/world/19jan2017/nato_ustav_5st.html?tema
Meanwhile, security breaches and data leaks are often results of serious security system flaws.
Criminals attacked computers in Poland's Ministry of Foreign Affairs by hijacking a server in Latin America and sending Ministry employees emails with a Trojan attached to them.
The Anti-virus Times recommends
Cybercrime doesn't have citizenship—it is multi-national and recognises no borders. Hackers from one country often operate on the territory of another country, where they are often captured and then extradited to the US. Those who don't read our issues carefully and feel admiration for hackers should remember that in US courts prison terms for each charge are added together—ad infinitum.


![Shared 1 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
vasvet
07:37:10 2018-07-22