A flash drive as a disguise
Monday, August 14, 2017
Normally when we see (or use) a removable media device, we think only about the files contained on it. But what is a file? It is a certain area on the media. Meanwhile, storage media can vary. If we’re dealing with a hard drive, we computer novices can't tell how many disks are used on the device or how data is written onto it, without reading labels.
So if we try to simply connect the media to a computer, the latter wouldn't be able to use it. A translator would be needed that allows the computer to understand what is written on the media. The “translator” lets you plug new devices into the appropriate ports without thinking about different media formats.
Let's use flash drives as an example. They work as follows:
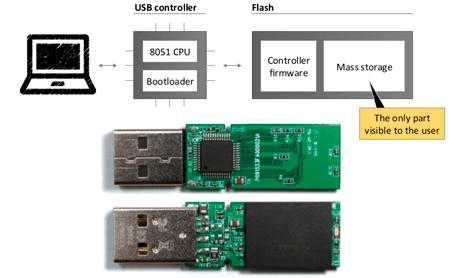
Unbeknownst to most users, every USB device features a control chip and the memory where its firmware is stored.
https://www.anti-malware.ru/analytics/Threats_Analysis/security-flaws-in-usb
When you plug a new flash drive into your computer, it gets a device ID, reads the USB controller's firmware, and uses its driver to write and record data onto the flash drive.
So, by connecting a flash drive to your machine, you are essentially making it download a driver from the media.
And it can be from any media.
And the system has no idea what the driver will do.
A fortune teller can only dream of gaining so much trust.
And here are a few examples of attacks.
Because the “translator” facilitates interaction between a flash drive and a computer, the media can assume any identity. It can pretend to be a keyboard, for example.
Perhaps, you’ve heard about RubberDucky or BashBunny, which look like ordinary USB sticks, but when connected to a PC, they will imitate pre-programmed keystrokes. Such devices can be used to download and launch a backdoor in just twenty seconds. An Android device can also be used in attacks of this kind.
https://www.anti-malware.ru/analytics/Threats_Analysis/security-flaws-in-usb
Or a new Ethernet adapter.
By posing as a USB Ethernet adapter, PoisonTap can hack into a locked/password-protected system. This attack is feasible because machines automatically send DHCP queries whenever a new Ethernet adapter appears in the system. The device responds to the request and informs the computer that the entire IPv4 address space belongs to its local network. After that, whenever the compromised system sends a packet to any IP address, it will always be transmitted via the USB-Ethernet device because the local subnet has higher priority than the gateway route of any other device.
In other words, thanks to OS features, a malicious flash drive makes the computer channel all inbound and outbound traffic through it. A dream come true for fraudsters and spies!
#Dr.Web_settings #security #removable_mediaThe Anti-virus Times recommends
- Use flash drives of unknown origin with caution. You may think you're dealing with a USB stick, but the device may in fact have an agenda of its own.
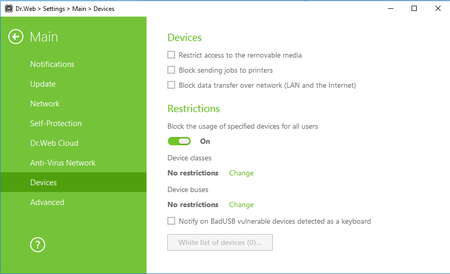
- Dr.Web can block pretenders of this kind. To automatically block devices posing as keyboards, go to the anti-virus's settings, select Main → Devices and tick the box Notify on BadUSB vulnerable devices detected as a keyboard.



![Shared 0 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
Alena Rawat
08:26:36 2019-07-27
Неуёмный Обыватель
05:17:30 2018-07-23
vasvet
07:17:51 2018-06-24
microsoftxbox
13:59:53 2017-08-30