Security is a strange thing
Wednesday, May 31, 2017
In our Anti-virus Times issues, we have repeatedly recommended to our users that they lower privileges when working with various devices, and, at the same time, we’ve warned them not to trust marketing experts extolling product technologies.
Researchers Matt Graeber and Matt Nelson found a new way to bypass the User Account Control feature in Windows, which was developed to prevent unauthorised changes from being made to the system.
After analysing a number of default tasks in the Windows 10 scheduler, the researchers found that one of the processes (SilentCleanup) can be launched by a non-privileged user, but is executed with elevated privileges. As the experts explained, the SilentCleanup file is associated with the Disk Cleanup utility or Cleanmgr.exe. When you run cleanmgr.exe, the process privileges automatically increase to the maximum level, which is associated with the settings defined in the task configuration.
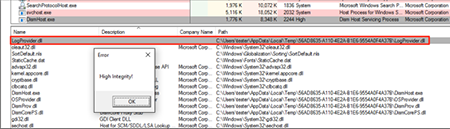
After you run the utility, Disk Cleanup creates a new folder—GUID in C:\Users\\AppData\Local\Temp, where several .dll files, as well as dismhost.exe, are copied. Once launched, dismhost.exe. starts unloading .dll files in a certain order from the folder—C: \ Users \\ AppData \ Local \ Temp \ <guid>. As the current user has write access to the % TEMP% directory, it is possible to spoof the .dll used by the dismhost.exe process.
The researchers passed their materials to Microsoft. However, the company noted that the UAC mechanism does not belong to the security features, and, accordingly, this problem cannot be considered to be a vulnerability.
https://enigma0x3.net/2016/07/22/bypassing-uac-on-windows-10-using-disk-cleanup/
What does this news tell us?
- Despite the fact that the user is working with lowered privileges, several utilities use far more elevated ones.
- Working with user privileges that differ from administrator ones is not a remedy, although that significantly reduces the risk of infection.
- Using the whitelist of allowed programs is not a remedy, either: the attack is carried out by substituting the library.
- Controlling the integrity of running applications is also not a panacea: the code is not injected into a running process—a process immediately starts up with malicious functionality.
The Anti-virus Times recommends
- Security is a strange thing. You can’t tell for sure whether it exists. No anti-virus can be a be-all, end-all solution that resolves all security problems. Security itself is based on the user's understanding of the consequences of their own actions.
- Using lowered privileges and the whitelist, controlling the integrity of processes—all of this can protect against the launch of new applications, against application features being changed on the fly. But only an anti-virus allows you to scan all new files and to guarantee that they are clean from known malicious programs. And if unknown threats are detected, it allows you to cure them after you get the updates.
Probably each of you has watched a movie where a character sleeps with a gun under their pillow. An anti-virus is that gun that allows you to put an end to attacks by criminals who bypass all the protection measures of your digital "flat".


![Shared 1 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
vasvet
06:54:25 2018-07-21
Неуёмный Обыватель
03:49:46 2018-07-21