Computers may sleep, but criminals do not!
Wednesday, April 26, 2017
Everyone knows that for a computer to get infected, someone has to press something or launch something, or at least neglect to install updates, which allows hackers to exploit existing vulnerabilities. It is also common knowledge that if a computer is turned off, no attacker will be able to penetrate it and make modifications (except if they have physical access).
The Anti-virus Times has already dispelled many myths. And now it’s time to do it once more.
It’s actually quite feasible to write data on a computer that has been turned off.
Our readers are unlikely to experience an attack of this kind, but you never know—after all, there was time when malware was regarded as just a theoretical possibility.
A while ago, Intel introduced its Intel vPro technology:
The Intel AMT technology (active management technology) within it facilitates access to a target machine even if it’s turned off.
Naturally, the system involved must have components capable of ensuring this possibility, and it must be connected to a power grid.
The Intel Q35 Express chipset was specifically designed to meet these requirements and incorporates a set of integrated components that includes the Management Engine (ME) and a gigabit Ethernet controller that works with the PHY-chip Nineveh 82566DM. This lets the chipset gain remote access to AMT data and settings stored in non-volatile memory, even when the computer is off.
The technology was intended for system administrators. Specifically, the feature described above could be used by administrators to remotely access computers that are off or won't boot up (e.g., due to infection or a damaged hard drive).
Two laptops with the Yonah CPU were used for a demonstration. One of the machines acted as a target computer, while the second one was supposedly used by a system administrator. The laptops were connected to a network. The target machine was infected with malware that rendered the operating system completely non-operational; even the network stack was inaccessible.
iAMT technology made it possible to access frozen machines over a special segment of network bandwidth. As a hardware feature, it didn't rely on connectivity the operating system was unable to provide. The main condition is that the target system's hardware must work properly. In this example, an administrator was able to remotely neutralise the malware and reboot the target machine. Moreover, in a corporate network, an administrator can automatically configure and distribute patches and updates between target machines—the employees will never suspect that some tasks are being performed in the background.
https://www.overclockers.ru/hardnews/19175/Intel_demonstriruet_rabotu_iAMT_na_primere_Yonah.html
http://www.thg.ru/mainboard/intel_vpro/print.html
http://compress.ru/article.aspx?id=18538
I especially like the fact that I can connect to a remote host via VNC, even if it has problems with Ethernet adapter drivers (after all, vPro operates on a lower level than the operating system), and use the VNC to install all the drivers I need.
The IDE-R feature can also be used to boot up from an external media as if a local hard drive is being used. That is to say, I can connect to the host via VNC, specify a boot image, and boot up a working OS.
The last one sounds really great—even if your operating system is well protected, someone can remotely boot up from another media and examine your data, and your security software will never know about it because the operating system hasn't been loaded!
#security #remote_access #technologiesThe Anti-virus Times recommends
There is no protection against some threats. However, in some situations certain threats appear to be hypothetical. New technologies emerge almost on a daily basis. Modern computers, operating systems, and programs have many features that we don't use. It is believed that the ordinary user utilises no more than 20% of their applications’ features or their computer as a whole. But this means we don't need the remaining 80%, which can present threats—threats we’ve already discussed on more than one occasion.
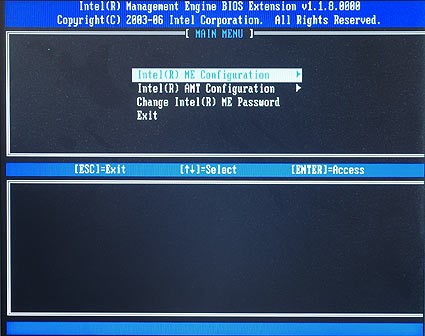
You can disable Intel vPro (if it’s on your computer) in the BIOS settings:


![Shared 3 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
Неуёмный Обыватель
03:05:04 2018-07-21
vasvet
08:34:55 2018-06-24
razgen
00:54:31 2017-04-27