Evil is secure
Monday, February 13, 2017
News outlets are full of reports about information privacy and big scandals caused by data leaks. This topic becomes particularly popular in the run up to elections. But politics aside, let's take a look at our own emails.
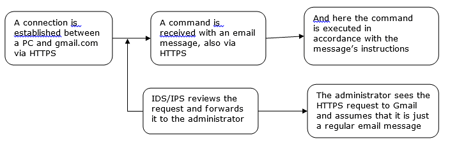
Let's say we've sent a message to a Gmail address. Wouldn’t you agree that that’s a normal thing to do? Let's take a look at the diagram.
In our news posts, we often mention that many malicious programs communicate with command and control servers. That's why any unsanctioned connection made between an accountant's computer and a node on the Internet that doesn't host a website is not a very good sign. It is quite possible that the connection was established by malware. To rule out incidents of this kind, experienced system administrators only allow inbound and outbound traffic over certain protocols in their corporate networks and can even restrict the number of sites that employees are allowed to visit.
But attackers know a way around this: to achieve their goals, they can use services whose traffic is allowed into a corporate network. Email is one such service. To commence an attack, intruders can register a mailbox on a popular mail server that provides protection from the keen eye of intelligence services (a highly demanded feature nowadays). As a result, an email sent by malware over a protected protocol will pass all security checks because the protocol safeguards data from anti-viruses and intelligence services with equal effectiveness. An administrator is most likely to disregard it too—after all office employees correspond via email a great deal. #corporate_security #email #SpIDer_Mail
The Anti-virus Times recommends
- It is system administrators who must install and configure mail clients on employee PCs. Employee personal preferences towards certain email clients should be disregarded—companies need their corporate standards.
- Employees should access email only using mail clients and never the web interface.
- A local firewall should be configured to only keep open those mail-related ports that are utilised to send and receive messages by the mail client that the organisation uses.
- Messages should only be sent via the company's mail server or mail proxy—sending messages directly to addresses outside the corporate network is not recommended. If the mail/proxy server can store outgoing emails, it may allow you to determine the source of an outbound message, if necessary.
- The anti-virus protecting employee PCs must be able to analyse HTTPS traffic. Otherwise, an unauthorised data transfer will most likely go undetected. In Dr.Web Security Space, the mail monitor Dr.Web SpIDer Mail is responsible for examining mail traffic. It can scan traffic transmitted via protected protocols.
- And of course, an anti-virus that will prevent malware from being installed in a system must be up and running on all corporate PCs and other devices.
Privacy is important, but you need to remember that criminals can take advantage of reliable, secure access to user data. And ultimately they benefit from your privacy!


![Shared 17 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
vasvet
07:48:40 2018-06-30
Mr.Pr
00:20:05 2017-02-14
please give us a review of DDoS Attacks that would be very interesting! :)