Password exchange
Tuesday, December 20, 2016
Many sci-fi stories describe body-exchange experiences, which is when a body’s new owner acquires all the abilities of that body’s previous owner. In reality, we can't do that just yet, but for many of our friends and business associates, we are little more than storage units for their electronic information—information that is relatively easy to access and modify.
I needed a document from my boss's computer. At the time, he was away on holiday, and colleagues advised me to just call him and ask him for his password (all logins followed the standard name.surname pattern). It took him a while to recall who I was, but eventually he divulged his password. After that, neither he nor any other employees monitored what I was doing on his computer. This happened on Friday. On Monday, my boss got back to work and didn't bother to change his compromised password. Interestingly, the password could be used to access the mailbox (no two-factor authentication had been set up) as well the internal campus account.
Sound familiar? While developers and engineers never stop devising more convenient authentication methods, passwords like 123456, written on sticky-notes and placed under keyboards, remain as persistent as before. And no one has ever given a thought to creating separate data storages on a family tablet.
That's why company management can often be very hard on those whose data has been compromised. The government has also stepped in.
On July 6, 2016, the United States Court of Appeals for the Ninth Circuit ruled that exchanging passwords violates the U.S. Computer Fraud and Abuse Act, CFAA. Typically, this Act applies in cases involving hacker attacks, so the Court's decision actually equates the exchange of passwords to a cybercrime.
According to the ruling by the United States Court of Appeals for the Ninth Circuit, the actions of Korn Ferry's employee David Nosal, who used his former colleague’s password to gain access to the company database, violate the CFAA.
Is the government’s concern over such a trifle as a password exchange between employees really justified? Well, Edward Snowden, who used his colleagues' passwords to collect data for his revelations, immediately comes to mind.
In most cases, company management neglects security measures that can be implemented to protect employee personal computers and mobile devices. Modern, progressive employers believe that their employees must work from any part of the globe and rely on their information security know-how. How unlikely would it be for a curious child to get hold of their daddy’s tablet, which has remote access to his company’s network, and then start formatting a server disk?
#corporate_security #password #Dr.Web_settings #Parental_ControlThe Anti-virus Times recommends
- A strong password is a necessity, and in the face of constant hacker attacks on sites we access with our password, we are compelled to change our passwords regularly. But do you remember all the sites you’ve accessed with your one-and-only password?
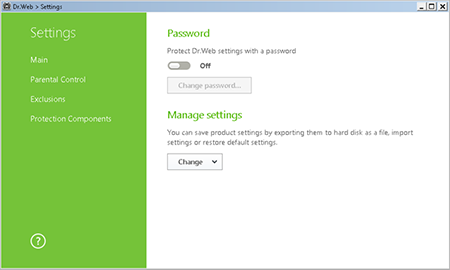
Alas, users like to disable anti-virus software or change its settings. Password-protecting the settings may help avoid this.
To set an access password, click on the icon
 ((it will now look like this:
((it will now look like this:  ); then click on the icon
); then click on the icon  , and in the Settings window, select Main. Toggle on the corresponding option, and click Change password.
, and in the Settings window, select Main. Toggle on the corresponding option, and click Change password.Important! Using a password that matches your user account on a computer is not recommended.
• You can take advantage of the Parental Control to establish access permissions for various computer components and websites. To learn how to do this, please refer to our other numerous publications. You can also use the component to “punish” naughty violators of the rules for working on a computer.
Parental Control settings can be defined individually for each user account on a single machine. To restrict Internet and computer usage time, click on the icon
 in the system tray; click on the padlock icon to unlock access to the settings
in the system tray; click on the padlock icon to unlock access to the settings  (it will now look like this:
(it will now look like this:  ); then click on the gear icon,
); then click on the gear icon,  and in the Settings menu, select Parental (Office) Control. In the newly appeared window, select the user account for which you want to adjust the settings. Then in the Time section, click Change.
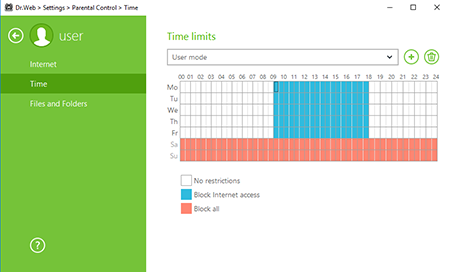
and in the Settings menu, select Parental (Office) Control. In the newly appeared window, select the user account for which you want to adjust the settings. Then in the Time section, click Change.The Time Limits window will open.
Use the time grid to create an access schedule. To do this, hover your cursor over any white square. Clicking once will make the square turn blue; clicking twice will make it turn maroon; and triple-clicking it will turn it white.
- Blue indicates that Internet access will be blocked during the time period specified.
- Maroon indicates that an account is blocked (the computer can't be used under that account).
- White indicates that there are no restrictions.
Once you click to the colour you want, hold the mouse button and move the cursor to change the colour for the time periods you need to define. This is how you can configure a working schedule for a particular user account.


![Shared 15 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
Неуёмный Обыватель
04:56:04 2018-08-24
vasvet
08:03:18 2018-06-30
eaglebuk
17:00:00 2017-02-19