How will you pay?
Friday, November 11, 2016
Malicious programs like encryption ransomware are created for the sole purpose of earning money illegally. Those who use programs of this kind are always looking for ways to conceal their earnings and turn them into cash.
- In the “golden era” of ransomware, extortionists ordered users to pay a ransom by sending chargeable SMS messages to short numbers. An upsurge of interest in transferring money that way was quickly noticed, and this method was curtailed.
After that criminals began ordering users to transfer money to mobile accounts rather than send SMS.
For various reasons, including the fact that their appetite had exceeded the limits of what amounts could be transferred, criminals abandoned this method for good.
- Then (and this scheme is still in use in Russia) attackers instructed users to transfer ransom payments to the accounts of fly-by-night companies or individuals. However, when robbing a bank, the trick is not to get caught! Hiring a “drop man” is one way to withdraw money. Drop men are used to withdraw money from ATMs.
Usually the money is split 50/50 between the hacker and the person handling the drop men. The handler divvies out a percentage of his share to each drop man.
http://24smi.org/news/8816-kak-xakeri-obnalichivaut-ukrad.html
- When cybercriminals set out to empty the pockets of EU users, they had to learn how to work with other currencies.
Once a system is infected, Trojan.Winlock.5490 displays a window containing a demand, written in French, to pay 100 euros via a Paysafecard or Ukash card. Then the card number entered by the victim is sent to the remote command server and the user is informed that the payment will be processed in 24 hours.
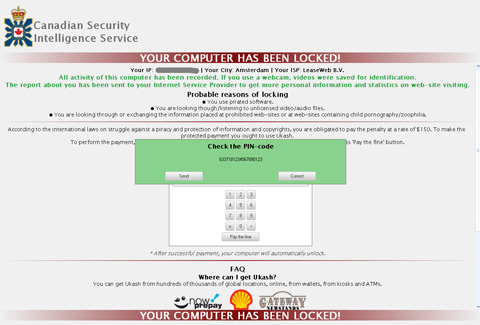
- Trojan.Winlock.7384 uses a configuration file that contains information about which countries and electronic money systems the Trojan can work with—typically, those systems are Ukash, Moneypack and Paysafecard.
To unlock the computer, the Trojan demands that the victim enter a ransom payment transaction code. The entered code is transmitted to the controlling server and validated. If the payment is confirmed, the control center commands the Trojan to unlock the computer. The amount to be paid for this service is 100 euros or 150 US dollars.
http://news.drweb.ru/show/?c=5&i=3025&lng=ru
However, one problem remained—how to cash Ukash, MoneyPak, and PaySafeCard cheques in Russia. Then a service for cashing cheques of this kind appeared on the market. Casinos and payment processing systems, such as Webmoney, accepted these cheques. But when ransomware locker activity reached epic proportions, Webmoney was quick to stop this practice.
New times bring new opportunities.
- Cryptocurrencies allow for complete anonymity and this has made them criminals' favourite tool. Of course, malicious mining programs exist, but, in most cases, criminals use bitcoins to receive a ransom.
Doctor Web issued a warning about Linux.Encoder.1 encryption ransomware which corrupts files on Linux machines. The ransom amount demanded equalled one bitcoin.
http://bitcoininfo.ru/news/hakery-shifrovalshchiki-trebuyut-vykup-v-bitkoinah-u-polzovateley-linux
Today criminals demand up to 1,500 bitcoins for decryption. 1 bitcoin equals 272 euros or 330 dollars. A ransom demand can reach 49,500 dollars.
The Anti-virus Times recommends
- In our digital world, banks keep no secrets from law enforcement agencies. Even banks in Switzerland.
Large Swiss banks (such as Credit Suisse, Julius Baer, Zuercher Kantonalbank, and a branch office of Britain’s HSBC) made an agreement with the US Department of Justice to turn over personal information as well as the recorded phone calls and email correspondence of 10,000 employees who assisted wealthy Americans in tax evasion schemes.
In February 2013, the Federal Act on International Administrative Assistance in Tax Matters came into force in Switzerland. The civil code, the law on forced debt collection, the bankruptcy law, the administrative law, and the criminal law include certain restrictions related to banking secrecy: information required can be disclosed under a court ruling without the customer's consent.
This is a warning for those who believe that they can hide their illicit income in a bank ☺.
- Times are changing; the desire to obtain money illegally remains. People are weak. So we will witness more than one wave of encryption ransomware attacks.
- In some cases (approximately 10 out of 100), Doctor Web can help victims.
Steps that users need to take if their systems become infected with encryption ransomware:
- Use the “Send a suspicious file” form to send an encrypted doc-file to the Doctor Web anti-virus laboratory.
- Wait for a reply from a support engineer and follow their instructions.
Things you shouldn't do:
- Change filename extensions for encrypted files—if you do this and a decryption key is found, the utility won't know which files require decryption.
- Use data recovery and decryption applications on your own without first consulting with our support engineers.
- Prepare in advance for a possible incident.
- Add the link to the Doctor Web technical support page to your browser bookmarks. (This is the page containing the form used to send files to the anti-virus laboratory.)
Learn in advance what data you will need to send to technical support. Otherwise, all the time the attackers give you to pay a ransom will be spent clarifying this.
Important! The full list of requirements can be found here: http://legal.drweb.com/encoder?lng=en.
- Use the Data Loss Prevention feature of Dr.Web Security Space to back up your important files in protected storage. Unlike ordinary backups, these are protected by the anti-virus, and neither criminals nor malware will be able to delete them. This can serve as an additional measure to protect your important information. And, if you don't back up your data by any other means, this will be the only protection you have.


![Shared 16 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
vasvet
06:21:53 2018-07-26