Hidden passwords: A loophole for hackers
Friday, September 23, 2016
Every day we use our account passwords in a local network or on our computers. We also set passwords for online services (even if we won’t remember them and they’re saved in our browser's password manager). But the passwords we know are just the tip of the iceberg.
Many programs that we use in our work—accounting software, CRM systems, video control systems, as well as access control systems—use built-in databases. However, they don’t implement database functionality on their own; instead they simply use a ready-made solution that is supplied as part of their product.
Let's suppose that you set a reliable password to access an application management console and update it regularly—as required by safety standards. But the database is an independent application. And it has its own access password, one that is usually installed by default and, therefore, known to hackers!
Now let's discuss how difficult it is to exploit this vulnerability. I believe that to manage this, hackers don’t need any special knowledge—a system can be compromised using readily accessible tools in just a few minutes.
Find the FireBird server
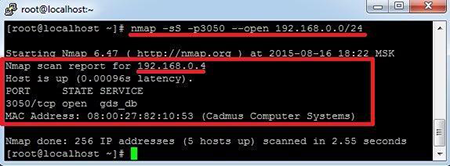
The first thing a cybercriminal will obviously do is search for a 3050/tcp port in a company's internal network. They just need to download nmap ( nmap.org/download.html) and run it with the following keys from the cmd console:nmap -sS -p3050 --open 192.168.0.0/24
In response, nmap will eventually display all open 3050/tcp ports found in network 192.168.0.0/24:
Thereafter, each port has its own network address, but the principle is the same. If you don’t want to go the nmap route, you can take advantage of other programs—most are graphical and accessible to everyday users. One of the open ports will belong to an ACS server. Most likely, there will be only one port (as shown in the screenshot), but let's imagine there are several of them.
Connect to FireBird
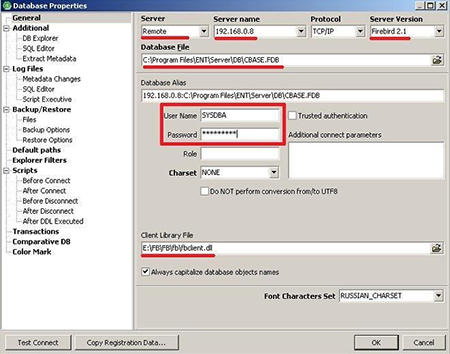
Once we’ve identified the FB ports, we need to connect to them. This can be done using the program IBExpert. Remember you will need an fbclient.dll library (you can obtain it by installing the FB server on your machine or downloading it from the Internet). Next, you need to consistently try to connect to each FB server. To connect to FB, you will need to know the login, password, and path to the database on the FB server. We know the login and the password since that’s the vulnerability, and with a very high degree of probability, we’ll discover that the path to the database is a standard one.
Thus, we’ve directly connected to the database and can do anything we want, even things the official administration interface doesn’t permit.
The Anti-virus Times recommends
Many programs offer to install additional components officially. This is not as safe as many may think. Only a controlled list of software should be used on employee machines.
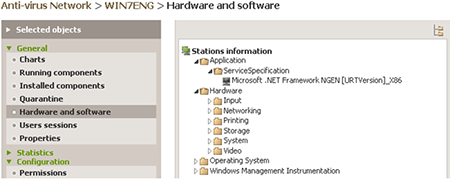
The Dr.Web Enterprise Security Suite Control Center will help you ascertain what programs are installed on computers.
The Dr.Web Enterprise Security Suite Control Center also incorporates a built-in database, but the documentation includes a recommendation on how to use an external database whose access permissions can be configured in a company’s best interests. The database can be used on the same server the Dr.Web Enterprise Security Suite Control Center is installed on, as well as on one other one. Database selection is virtually unrestricted, and they can be installed on any operating system the company uses. Note that the training course DWCERT-002-ESS10 contains the following text:
Important! Do not set the password provided in the example. For commercial use it is recommended that you create a cryptographically strong password to maintain security. It must include a minimum of eight characters. Use the command
makepasswd –chars=12to create a cryptographically strong pseudo-random password. You must remember the password, because in the future it will be used to connect to the database.If you use Dr.Web Security Suite, it is recommended that you password-protect the anti-virus settings.
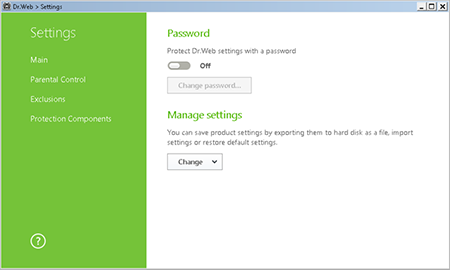
To set an access password, click the icon
 (the icon will change to
(the icon will change to  ) and click on the newly appeared icon
) and click on the newly appeared icon  , in the Settings menu, select General. Click on the toggle, and then on the button Change password.
, in the Settings menu, select General. Click on the toggle, and then on the button Change password.Specify password.


![Shared 15 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
Неуёмный Обыватель
03:54:59 2018-08-21
vasvet
07:17:51 2018-07-22