Password: when everything depends on one word
Thursday, August 18, 2016
Carelessness does more harm than a want of knowledge.
— Benjamin Franklin
To access many services on the Internet, you need a login, password, and email address. Yet news outlets are full of reports about data leaks occurring on various sites.
Even if a leak is discovered quickly and all user passwords are forced to change, the problems don’t end there. Criminals can use the leaked information to access other services that include:
- Social networking sites where criminals can send “friends” links to bogus sites;
- Mailboxes that can also be used to send out spam and mount phishing attacks;
- Payment processing services;
- Cloud data storage to plant malicious files that will later be downloaded by victims onto their machines.
Leaked authorisation information translates into profits for criminals and problems for users!
The following are the most frequent causes of password leaks that sooner or later will lead to the disclosure of user information.
- A poorly configured anti-virus (updates not applied regularly) or the absence of one on a machine gives Trojans free rein to steal whatever they want.
- Site security issues, negligence, or malice on the part of the web portal's staff.
- Social engineering techniques (e.g., phishing) that trick users into divulging their data to criminals.
- The carelessness of users.
A cautious person makes sure their passwords are safe regardless of any security guarantees from site owners.
And what about you—are you cautious?
Troy Hunt from Microsoft launched the site https://haveibeenpwned.com/, which aggregates information about all known hacking and data leak incidents. This site was created after the largest-to-date attack occurred when data from 153 million Adobe user accounts (a number bigger than the population of Russia!) appeared in the public domain. The information included user names, email addresses, encrypted passwords, and password hints—all in plain text. Furthermore, the passwords weren't encrypted very well, so many of them were unscrambled rather quickly.
You can use this site to check whether your email address or login have ever been compromised. If they have, it’s high time to change your password(s).
Sites about data leaks can be compromised too.
The site https://pwnedlist.com/ offered users the ability to check whether their passwords had ever been compromised. The service was available free of charge to individuals, while companies could use it on a payment basis.
Data from this site was leaked, too. The blow to its reputation was so devastating that it was scheduled to close down on May 16, 2016.
The Anti-virus Times recommends
- Do not use the same password on different sites. If you find it difficult to memorise several passwords, add several easy-to-remember characters to the beginning or the end of a base password. Obtaining a password by means of a brute-force attack takes much more time than cracking a stolen password hash, so a criminal who operates on a large scale may give up if the first attempt to steal your information fails.
- Monitor IT security news the way you follow weather forecasts. If a site you visit or used to visit has been compromised, make sure that your data hasn't been compromised.
- If, after hearing about a data leak, you go on the affected site and it asks you to verify the integrity of your data, use common sense. If you are asked to enter a password or your credit card information, you are most likely dealing with fraudsters.
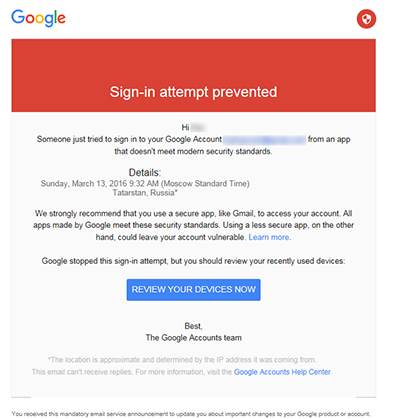
- If the sites you visit offer enhanced security measures, such as, for example, making it impossible to sign in from two or more devices, only allowing sign-ins from a specific IP address, requiring that a texted code be used to log in, etc., take advantage of them. In the worst-case scenario, this will allow you to instantly detect an attempt to gain unauthorised access to your data; promptly change your password; and, best of all, stop the attack.


![Shared 15 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
vasvet
19:18:22 2018-07-02