Through a flash drive and onwards to the target
Friday, August 18, 2017
According to a common information security joke, the best way to keep a system secure is to shut it down, put it in a cave, and barricade the entrance. However, we've already seen that, under certain circumstances, even a machine that has been shut down can be controlled—using Intel AMT. And how about complete isolation?
Computers that aren’t connected to an intranet or the Internet are a common phenomenon. Machines of this kind can, for example, be used to process sensitive information.
Pirates believe that anti-viruses scan local networks to find machines using the same anti-virus key file. We’re not going to disprove this. Let's just say that the presence of an undocumented feature would prevent anti-virus software from passing certification because that process involves rigorous testing to make sure no undocumented features are included in the software.
If a computer doesn't receive data from other nodes (input is only conducted via a keyboard or other peripheral devices that are always connected to it), it can still get infected, but to accomplish that, an attacker would need to exploit some sort of hardware backdoor.
However, removable media is normally used to transfer data between isolated machines and the network. And by “media” we usually mean flash drives.
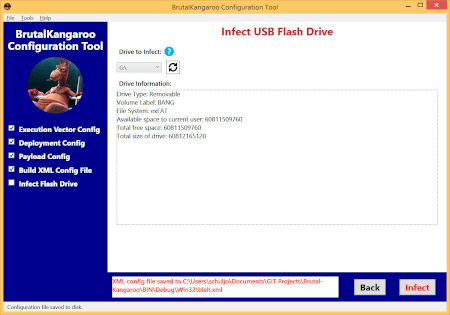
On June 22, 2017, WikiLeaks published documentation related to the Brutal Kangaroo tool suite. This toolset for Windows uses flash drives to help infect air-gapped computers.
The Brutal Kangaroo suite incorporates the following components:
- Drifting Deadline: a thumb drive infection tool.
- Shattered Assurance: server software that facilitates the automatic infection of thumb drives and spreads Brutal Kangaroo. Individual thumb drives are infected using Drifting Deadline.
- Broken Promise: a Brutal Kangaroo post processor.
- Shadow: the main persistence mechanism. This is a stage 2 tool. It is used to create a covert network inside targeted closed networks.
To run Brutal Kangaroo, a computer must have .Net 4.5 installed on it.
The last phrase brings up memories of viruses for MS-DOS.
Back then, their authors tried very hard to reduce the size of their programs if only by a single byte. Nowadays, malware doesn’t just infect systems;
it also has certain system requirements.
It’s very picky.
How does other NSA software steal or modify information? The same way other malicious programs do:
- A system gets infected after a brute-force or phishing attack or by some other means.
The initial infection occurred because the anti-virus on an employee's PC was either disabled or was using outdated virus definitions, allowing malware to be launched from a phishing email containing documents.exe.
Please note that the anti-virus software had detected the malicious attachments as well as the attackers' activities in the compromised systems—long before any money was stolen. Among all the other things detected was suspicious behaviour on the part of the legitimate program Ammyy Admin. In some cases infection was prevented by the anti-virus software.
- Awaiting a connection between the infected computer and removable media.
- Infecting media.
Doctor Web reports a significant increase in new malware spreading via removable data storage devices. The scripts make use of code obfuscation which complicates their analysis.
Under the Dr.Web classification system, this malicious code is called Win32.HLLW.Autoruner.
- Infecting other servers and PCs via an infected flash drive or another removable media device.
It’s quite obvious that this method can be successfully applied only if writing data on removable media and the autorun feature aren't disabled. Nonetheless, this infection technique is quite popular. For example, banking Trojans that infect cash points use it quite often.
The spyware's parameters can be changed.
An operator selects which spyware modules will be written onto a thumb drive and also specifies what information needs to be collected from a victim’s computer and written onto the flash drive. A filename template is used to define what files need to be collected. An operator can also define the maximum volume for the collected data as well as the amount of free space that must remain on the thumb drive (apparently, to avoid suspicion). The format in which the gathered data should be written is specified too. For example, everything can be written into an existing file (e.g., .jpg or .png) or an NTFS data stream that will be hidden from users. Also specified are the maximum number of spyware launches, the launching conditions (e.g., only when an administrator is signed into the system), and the blacklisted processes in whose presence the program mustn't be started.
Interestingly, a rare malicious species—a malicious program for iOS—also spreads over removable media.
If a smartphone or tablet is connected to a desktop or laptop over a USB data cable, Trojan.AceDeceiver.2 automatically installs IPhoneOS.AceDeceiver onto the mobile device. To accomplish this, it leverages a vulnerability in Apple’s AirPlay DRM protocol.
The Anti-virus Times recommends
Absolute security is an unattainable ideal. Claims that certain servers are completely protected because only competent administrators have access to them can create a dangerous illusion of security because attackers can find and abuse vulnerabilities and/or configuration errors. If either of the two is present, sooner or later an anti-virus scan will reveal a Trojan on the server.
So you need an anti-virus even if your computer is air gapped. Just in case. And all sorts of things can happen.
Interestingly, Dr.Web can be updated in air-gapped networks as well as in those connected to the World Wide Web. Your Dr.Web anti-virus software will always be up-to-date.


![Shared 0 times [Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
Tell us what you think
To leave a comment, you need to log in under your Doctor Web site account. If you don't have an account yet, you can create one.
Comments
ka_s
18:40:03 2020-01-13
Неуёмный Обыватель
05:20:37 2018-07-23
vasvet
12:09:13 2018-07-15